Linux Wireless
Existing Linux Wireless drivers
Linux Support for Intel® Wireless Adapters
Linux drivers are part of the upstream Linux* kernel. They're available through the regular channels, distributions, or the Linux* kernel archives.The wireless device requires firmware to operate. Firmware usually ships with your distribution, or you can download it from the firmware git tree.
To install firmware:
- Copy the files into the distribution-specific firmware directory, /lib/firmware.
- If the directory doesn't work, refer to your distribution documentation.
- If you configure the kernel yourself, make sure firmware loading is enabled.
Linux Wireless
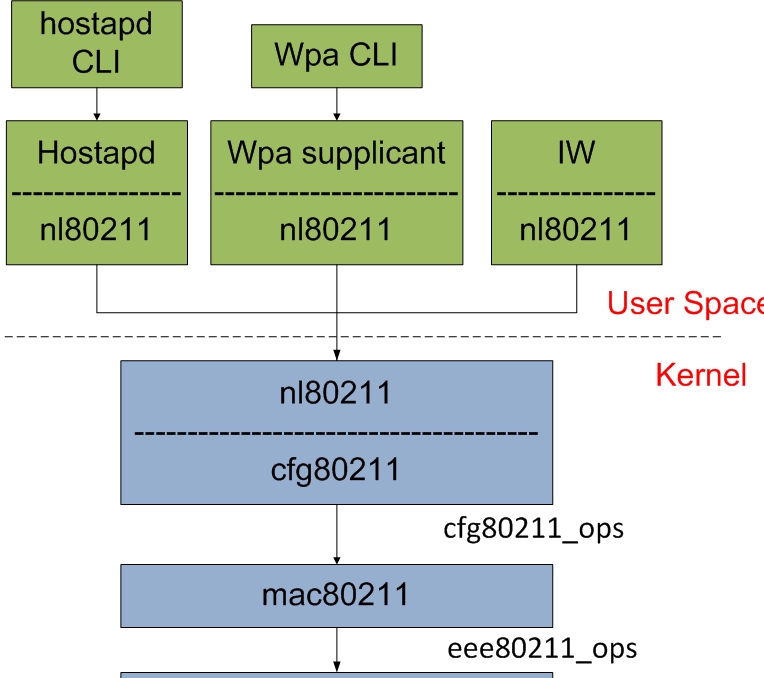
This site covers all the new 802.11 drivers, the new core mac80211 and cfg80211 components along with the new userspace and in-kernel nl80211 configuration interface. New nl80211 userspace applications are also documented.
reference
Git guide for Linux wireless users and developers
The latest Linux wireless development happens in two trees:
- mac80211-next
- wireless-drivers-next
Wireless-testing is the development repository that contains the latest Wireless communications source code of the Linux kernel. This repository usually contains the latest accepted upstream patches for wireless.
Cloning latest wireless-testing
git clone git://git.kernel.org/pub/scm/linux/kernel/git/wireless/wireless-testing.git cd wireless-testing
nl80211
nl80211 is the new 802.11 netlink interface public header.
Together with cfg80211 it is intended to replace Wireless-Extensions. nl80211 and cfg80211 are still under development.
- The nl80211 interface can be found in include/linux/nl80211.h
enumnl80211_commands {
/* don't change the order or add anything between, this is ABI! */
NL80211_CMD_UNSPEC,
NL80211_CMD_GET_WIPHY,
NL80211_CMD_SET_WIPHY,
…
…
NL80211_CMD_UNEXPECTED_4ADDR_FRAME,
NL80211_CMD_SET_NOACK_MAP,
/* add new commands above here */
/* used to define NL80211_CMD_MAX below */
__NL80211_CMD_AFTER_LAST,
NL80211_CMD_MAX = __NL80211_CMD_AFTER_LAST -1
};
enumnl80211_attrs {
/* don't change the order or add anything between, this is ABI! */
NL80211_ATTR_UNSPEC,
NL80211_ATTR_WIPHY,
NL80211_ATTR_WIPHY_NAME,
…
NL80211_ATTR_DISABLE_HT,
NL80211_ATTR_HT_CAPABILITY_MASK,
NL80211_ATTR_NOACK_MAP,
/* add attributes here, update the policy in nl80211.c */
__NL80211_ATTR_AFTER_LAST,
NL80211_ATTR_MAX = __NL80211_ATTR_AFTER_LAST -1
};
iw
iw is a new nl80211 based CLI configuration utility for wireless devices. It supports all new drivers that have been added to the kernel recently. The old tool iwconfig, which uses Wireless Extensions interface, is deprecated and it's strongly recommended to switch to iw and nl80211.
Getting iw
- Release tarballs
http://kernel.org/pub/software/network/iw/
http://git.kernel.org/?p=linux/kernel/git/jberg/iw.git
Build requirements
- libnl >= libnl1
- libnl-dev >= libnl-dev-1
iw help
Usage: iw [options] command Options: --debug enable netlink debugging --version show version (4.14)Commands:
- shows information about all physical wireless adapters
$ sudo iw phy Wiphy phy0 max # scan SSIDs: 4 max scan IEs length: 2243 bytes ... Supported interface modes: * IBSS * managed * AP * AP/VLAN * monitor * mesh point ... Device supports active monitor (which will ACK incoming frames) Device supports configuring vdev MAC-addr on create. Device supports VHT-IBSS.
iw dev phyname interface add name type type [mesh_id meshid] [4addr on|off] [flags flag*] [addr mac-addr]
- type managed, ibss, monitor, mesh, wds.
- flags The flags are only used for monitor interfaces
- mesh_id The mesh_id is used only for mesh mode.
iw dev wlx2c4d54ccfca6 interface add mon0 type monitorAn, bring it up,
sudo ip link set mon0 upThe newly created virtual interface "mon0" can be seen immediately, use
$ sudo iw dev phy#0 Interface mon0 ifindex 4 wdev 0x2 addr 2c:4d:54:cc:fc:a6 type monitor txpower 3.00 dBm Interface wlx2c4d54ccfca6 ifindex 3 wdev 0x1 addr 2c:4d:54:cc:fc:a6 type managed txpower 3.00 dBmA monitor interface in mac80211 uses radiotap to pass up to userspace additional data.
The following are monitor flags you can specify:
- none
- fcsfail FCS (Frame Check Sequence) is the checksum of the frame (CRC32), to make sure it was received correctly. By default, a driver should only forward valid frames to the monitor mode interface. This flag allow you to receive frame that also fail the test. One of the use could be monitoring the quality of a wireless network.
- plcpfail
- control Control frames help facilitate the transmission of frame between devices (ACK, RTS, CTS, etc). This is hardware-dependent.
- otherbss It would allow receiving frames from other BSS (other than the ones to/from the access point the card is connected to or the clients this access point is serving).
- cook
- active
iw dev mon0 del
iw list
iw reg set countryCodeYou can also use the latest wpa_supplicant (as of 0.6.7) now to change your regulatory domain, to do so just add a “country=US” entry into your configuration for example.
To get your current regulatory:
iw reg get
$ sudo iw dev wlan0 scan
iw event -f -t
- -t - print timestamp
- -r - print relative timstamp
- -f - print full frame for auth/assoc etc.
iw list
iw dev wlan0 link
iw wlan0 connect foo
iw dev wlan1 station dump
sudo iw dev wlan1 station get [peer-MAC-address][peer-MAC-address] would be the MAC address of your AP.
It does this by masking in the allowed bitrates, and also lets you clear the mask.
- Modifying tx legacy bitrates using only certain legacy bitrates
iw dev wlan1 set bitrates legacy-2.4 12 18 24
iw dev wlan1 set bitrates mcs-5 4 iw dev wlan1 set bitrates mcs-2.4 10 # To clear all tx bitrates and set things back to normal: iw dev wlan1 set bitrates mcs-2.4 iw dev wlan1 set bitrates mcs-5
iw dev wlan1 set txpower [auto|fixed|limit] [tx power in mBm]Note that the value this commands takes is in millibel-milliwatts (mBm). [power in mBm] = 100 * [power in dBm]
sudo iw dev wlan1 set power_save onTo query the current power save settings you can use:
iw dev wlan1 get power_save
Developers' documentation for wpa_supplicant and hostapd
The source code and read-only access to the combined wpa_supplicant and hostapd Git repository is available:
- Latest release
- git
git clone git://w1.fi/srv/git/hostap.gitHost AP driver is now maintained with the rest of the Linux kernel tree
wpa_supplicant
wpa_supplicant is a WPA Supplicant and SME (initiates MLME commands)
The design goal for wpa_supplicant was to use hardware, driver, and OS independent, portable C code for all WPA functionality.
wpa_supplicant is designed to be a "daemon" program that runs in the background and acts as the backend component controlling the wireless connection.
wpa_supplicant implements a control interface that can be used by external programs to control the operations of the wpa_supplicant daemon and to get status information and event notifications. There is a small C library that provides helper functions to facilitate the use of the control interface.

wpa_supplicant supports separate frontend programs and a text-based frontend (wpa_cli) and a GUI (wpa_gui, built on top of the Qt library from Qt ) are included with wpa_supplicant.
wpa_supplicant is initially configured using a text file "wpa_supplicant.conf" that lists all accepted networks and security policies, including pre-shared keys.
In most common cases, wpa_supplicant is started with:
wpa_supplicant -D nl80211 -i wlan0 -c /etc/wpa_supplicant.confWhere the parameters mean:
- -D: Driver to use
- -i: Interface to listen on
- -c: Path to configuration file
Configuring wpa_cupplicant
by file
wpa_supplicant is configured using a text file that lists all accepted networks and security policies, including pre-shared keys.See /usr/share/doc/wpa_supplicant/examples/wpa_supplicant.conf for detailed information about the configuration format and supported fields.
- mode: IEEE 802.11 operation mode
- 0 infrastructure (Managed) mode, i.e., associate with an AP (default)
- 1 IBSS (ad-hoc, peer-to-peer)
- 2 AP (access point)
- security
- auth_alg: list of allowed IEEE 802.11 authentication algorithms
- OPEN Open System authentication (required for WPA/WPA2)
- SHARED Shared Key authentication (requires static WEP keys)
- LEAP LEAP/Network EAP (only used with LEAP)
- key_mgmt: list of accepted authenticated key management protocols
- WPA-PSK WPA pre-shared key (this requires 'psk' field)
- WPA-EAP WPA using EAP authentication
- IEEE8021X IEEE 802.1X using EAP authentication and (optionally) dynamically generated WEP keys
- NONE WPA is not used; plaintext or static WEP could be used
- FT-PSK Fast BSS Transition (IEEE 802.11r) with pre-shared key
- FT-EAP Fast BSS Transition (IEEE 802.11r) with EAP authentication
- FT-EAP-SHA384 Fast BSS Transition (IEEE 802.11r) with EAP authentication and using SHA384
- WPA-PSK-SHA256 Like WPA-PSK but using stronger SHA256-based algorithms
- WPA-EAP-SHA256 Like WPA-EAP but using stronger SHA256-based algorithms
- SAE Simultaneous authentication of equals; pre-shared key/password -based authentication with stronger security than WPA-PSK especially when using not that strong password; a.k.a. WPA3-Personal
- FT-SAE SAE with FT
- WPA-EAP-SUITE-B Suite B 128-bit level
- WPA-EAP-SUITE-B-192 Suite B 192-bit level
- OSEN Hotspot 2.0 Rel 2 online signup connection
- FILS-SHA256 Fast Initial Link Setup with SHA256
- FILS-SHA384 Fast Initial Link Setup with SHA384
- FT-FILS-SHA256 FT and Fast Initial Link Setup with SHA256
- FT-FILS-SHA384 FT and Fast Initial Link Setup with SHA384
- OWE Opportunistic Wireless Encryption (a.k.a. Enhanced Open)
- DPP Device Provisioning Protocol
- psk: WPA preshared key; 256-bit pre-shared key.
- proto: list of accepted protocols
- WPA WPA/IEEE 802.11i/D3.0
- RSN WPA2/IEEE 802.11i (also WPA2 can be used as an alias for RSN).
- pairwise: List of acceptable pairwise (unicast) ciphers for WPA; one or more of:
- CCMP AES in Counter mode with CBC-MAC, RFC 3610, IEEE 802.11i/D7.0
- TKIP Temporal Key Integrity Protocol, IEEE 802.11i/D7.0
- NONE deprecated
- group: List of acceptable group (multicast) ciphers for WPA; one or more of:
- CCMP AES in Counter mode with CBC-MAC, RFC 3610, IEEE 802.11i/D7.0
- TKIP Temporal Key Integrity Protocol, IEEE 802.11i/D7.0
- WEP104 WEP with 104-bit key
- WEP40 WEP with 40-bit key
The key used when key_mgmt=WPA-PSK .
ASCII passphrase must be between 8 and 63 characters (inclusive). Separate tool, wpa_passphrase, can be used to generate 256-bit keys from ASCII passphrase. This field is not needed, if WPA-EAP is used.
Note that RSN is used also for WPA3.
proto=RSN
key_mgmt=WPA-PSK
pairwise=CCMP
group=TKIP
by DBUS API
Ubuntu doesn't use that configuration file at all.
wpa_supplicant doesn't run with a conf file.
It's a daemon that communicates with your Network Manager using DBUS.
If you use NetworkManager to configure your wifi connections, look at /etc/NetworkManager/system-connections for all your configured network connections.
It's all remotely controlled through the DBUS api.
/etc/dbus-1/system.d/wpa_supplicant.conf
wpa_cli
The wpa_cli command can be used to interact with wpa_supplicant.
It can be used to query current status, change configuration, trigger events, and request interactive user input.
$ wpa_cli ... Selected interface 'p2p-dev-wlan0' Interactive mode
- show usage help
> help
> interface wlan0 Connected to interface 'wlan0.
$ wpa_cli ifname
Selected interface 'wlp0s20f3'
$ sudo wpa_cli list_networks
Selected interface 'wlp0s20f3'
network id / ssid / bssid / flags
0 guest any [CURRENT]
> status
bssid=a4:56:30:cc:0f:30
freq=2462
ssid=Canonical-2.4GHz-g
id=0
mode=station
wifi_generation=4
pairwise_cipher=CCMP
group_cipher=TKIP
key_mgmt=WPA2-PSK
wpa_state=COMPLETED
ip_address=10.101.46.66
address=34:2e:b7:a8:96:f2
uuid=c455d25c-0f6c-5253-8daa-4f5c2e04ba25
> scan
> scan_results
$ wpa_cli get_capability eap/pairwise/group/key_mgmt/proto/auth_alg/channels/freq/modes
$ sudo wpa_cli -i wlan0 dump
ctrl_interface=/run/wpa_supplicant
...
$ sudo wpa_cli -i wlan0 get ctrl_interface
/run/wpa_supplicant
set
$ sudo wpa_cli -i wlan0 driver_flags
00000000BA0CFAC0:
AP
SET_KEYS_AFTER_ASSOC_DONE
P2P_CONCURRENT
P2P_CAPABLE
AP_TEARDOWN_SUPPORT
P2P_MGMT_AND_NON_P2P
SANE_ERROR_CODES
OFFCHANNEL_TX
BSS_SELECTION
TDLS_SUPPORT
SAE
IBSS
RADAR
DEDICATED_P2P_DEVICE
AP_CSA
$ sudo wpa_cli -i wlan0 set_network 0 ssid '"haha"'
OK
$ sudo wpa_cli -i wlan0 set_network 0 key_mgmt WPA-PSK
OK
$ sudo wpa_cli -i wlan0 set_network 0 psk '"12345678"'
$ wpa_cli list_sta
$ wpa_cli save_config
$ wpa_cli reconfigure
$ wpa_cli -i wlan0 enable_network 0
$ wpa_cli -i wlan0 disable_network 0
terminate
quit
ping = pings wpa_supplicant
relog = re-open log-file (allow rolling logs)
note <text> = add a note to wpa_supplicant debug log
mib = get MIB variables (dot1x, dot11)
level <debug level> = change debug level
logon = IEEE 802.1X EAPOL state machine logon
logoff = IEEE 802.1X EAPOL state machine logoff
pmksa = show PMKSA cache
pmksa_flush = flush PMKSA cache entries
pmksa_get <network_id> = fetch all stored PMKSA cache entries
pmksa_add <network_id> <BSSID> <PMKID> <PMK> <reauth_time in seconds> <expiration in seconds> <akmp> <opportunistic> = store PMKSA cache entry from external storage
reassociate = force reassociation
reattach = force reassociation back to the same BSS
preauthenticate <BSSID> = force preauthentication
identity <network id> <identity> = configure identity for an SSID
password <network id> <password> = configure password for an SSID
new_password <network id> <password> = change password for an SSID
pin <network id> <pin> = configure pin for an SSID
otp <network id> <password> = configure one-time-password for an SSID
psk_passphrase <network id> <PSK/passphrase> = configure PSK/passphrase for an SSID
passphrase <network id> <passphrase> = configure private key passphrase
for an SSID
sim <network id> <pin> = report SIM operation result
bssid <network id> <BSSID> = set preferred BSSID for an SSID
blacklist <BSSID> = add a BSSID to the blacklist
blacklist clear = clear the blacklist
blacklist = display the blacklist
log_level <level> [<timestamp>] = update the log level/timestamp
log_level = display the current log level and log options
select_network <network id> = select a network (disable others)
add_network = add a network
remove_network <network id> = remove a network
list_creds = list configured credentials
add_cred = add a credential
remove_cred <cred id> = remove a credential
set_cred <cred id> <variable> <value> = set credential variables
get_cred <cred id> <variable> = get credential variables
disconnect = disconnect and wait for reassociate/reconnect command before
connecting
reconnect = like reassociate, but only takes effect if already disconnected
abort_scan = request ongoing scan to be aborted
bss <<idx> | <bssid>> = get detailed scan result info
interface_add <ifname> <confname> <driver> <ctrl_interface> <driver_param>
<bridge_name> <create> <type> = adds new interface, all parameters but
<ifname> are optional. Supported types are station ('sta') and AP ('ap')
interface_remove <ifname> = removes the interface
interface_list = list available interfaces
ap_scan <value> = set ap_scan parameter
scan_interval <value> = set scan_interval parameter (in seconds)
bss_expire_age <value> = set BSS expiration age parameter
bss_expire_count <value> = set BSS expiration scan count parameter
bss_flush <value> = set BSS flush age (0 by default)
ft_ds <addr> = request over-the-DS FT with <addr>
wps_pbc [BSSID] = start Wi-Fi Protected Setup: Push Button Configuration
wps_pin <BSSID> [PIN] = start WPS PIN method (returns PIN, if not hardcoded)
wps_check_pin <PIN> = verify PIN checksum
wps_cancel Cancels the pending WPS operation
wps_nfc [BSSID] = start Wi-Fi Protected Setup: NFC
wps_nfc_config_token <WPS|NDEF> = build configuration token
wps_nfc_token <WPS|NDEF> = create password token
wps_nfc_tag_read <hexdump of payload> = report read NFC tag with WPS data
nfc_get_handover_req <NDEF> <WPS> = create NFC handover request
nfc_get_handover_sel <NDEF> <WPS> = create NFC handover select
nfc_report_handover <role> <type> <hexdump of req> <hexdump of sel> = report completed NFC handover
wps_reg <BSSID> <AP PIN> = start WPS Registrar to configure an AP
wps_ap_pin [params..] = enable/disable AP PIN
wps_er_start [IP address] = start Wi-Fi Protected Setup External Registrar
wps_er_stop = stop Wi-Fi Protected Setup External Registrar
wps_er_pin <UUID> <PIN> = add an Enrollee PIN to External Registrar
wps_er_pbc <UUID> = accept an Enrollee PBC using External Registrar
wps_er_learn <UUID> <PIN> = learn AP configuration
wps_er_set_config <UUID> <network id> = set AP configuration for enrolling
wps_er_config <UUID> <PIN> <SSID> <auth> <encr> <key> = configure AP
wps_er_nfc_config_token <WPS/NDEF> <UUID> = build NFC configuration token
ibss_rsn <addr> = request RSN authentication with <addr> in IBSS
sta <addr> = get information about an associated station (AP)
all_sta = get information about all associated stations (AP)
deauthenticate <addr> = deauthenticate a station
disassociate <addr> = disassociate a station
chan_switch <cs_count> <freq> [sec_channel_offset=] [center_freq1=] [center_freq2=] [bandwidth=] [blocktx] [ht|vht] = CSA parameters
suspend = notification of suspend/hibernate
resume = notification of resume/thaw
roam <addr> = roam to the specified BSS
p2p_find [timeout] [type=*] = find P2P Devices for up-to timeout seconds
p2p_stop_find = stop P2P Devices search
p2p_asp_provision <addr> adv_id=<adv_id> conncap=<conncap> [info=<infodata>] = provision with a P2P ASP Device
p2p_asp_provision_resp <addr> adv_id=<adv_id> [role<conncap>] [info=<infodata>] = provision with a P2P ASP Device
p2p_connect <addr> <"pbc"|PIN> [ht40] = connect to a P2P Device
p2p_listen [timeout] = listen for P2P Devices for up-to timeout seconds
p2p_group_remove <ifname> = remove P2P group interface (terminate group if GO)
p2p_group_add [ht40] = add a new P2P group (local end as GO)
p2p_group_member <dev_addr> = Get peer interface address on local GO using peer Device Address
p2p_prov_disc <addr> <method> = request provisioning discovery
p2p_get_passphrase = get the passphrase for a group (GO only)
p2p_serv_disc_req <addr> <TLVs> = schedule service discovery request
p2p_serv_disc_cancel_req <id> = cancel pending service discovery request
p2p_serv_disc_resp <freq> <addr> <dialog token> <TLVs> = service discovery response
p2p_service_update = indicate change in local services
p2p_serv_disc_external <external> = set external processing of service discovery
p2p_service_flush = remove all stored service entries
p2p_service_add <bonjour|upnp|asp> <query|version> <response|service> = add a local service
p2p_service_rep asp <auto> <adv_id> <svc_state> <svc_string> [<svc_info>] = replace local ASP service
p2p_service_del <bonjour|upnp> <query|version> [|service] = remove a local service
p2p_reject <addr> = reject connection attempts from a specific peer
p2p_invite <cmd> [peer=addr] = invite peer
p2p_peers [discovered] = list known (optionally, only fully discovered) P2P peers
p2p_peer <address> = show information about known P2P peer
p2p_set <field> <value> = set a P2P parameter
p2p_flush = flush P2P state
p2p_cancel = cancel P2P group formation
p2p_unauthorize <address> = unauthorize a peer
p2p_presence_req [<duration> <interval>] [<duration> <interval>] = request GO presence
p2p_ext_listen [<period> <interval>] = set extended listen timing
p2p_remove_client <address|iface=address> = remove a peer from all groups
vendor_elem_add <frame id> <hexdump of elem(s)> = add vendor specific IEs to frame(s)
0: Probe Req (P2P), 1: Probe Resp (P2P) , 2: Probe Resp (GO), 3: Beacon (GO), 4: PD Req, 5: PD Resp, 6: GO Neg Req, 7: GO Neg Resp, 8: GO Neg Conf, 9: Inv Req, 10: Inv Resp, 11: Assoc Req (P2P), 12: Assoc Resp (P2P)
vendor_elem_get <frame id> = get vendor specific IE(s) to frame(s)
0: Probe Req (P2P), 1: Probe Resp (P2P) , 2: Probe Resp (GO), 3: Beacon (GO), 4: PD Req, 5: PD Resp, 6: GO Neg Req, 7: GO Neg Resp, 8: GO Neg Conf, 9: Inv Req, 10: Inv Resp, 11: Assoc Req (P2P), 12: Assoc Resp (P2P)
vendor_elem_remove <frame id> <hexdump of elem(s)> = remove vendor specific IE(s) in frame(s)
0: Probe Req (P2P), 1: Probe Resp (P2P) , 2: Probe Resp (GO), 3: Beacon (GO), 4: PD Req, 5: PD Resp, 6: GO Neg Req, 7: GO Neg Resp, 8: GO Neg Conf, 9: Inv Req, 10: Inv Resp, 11: Assoc Req (P2P), 12: Assoc Resp (P2P)
wfd_subelem_set <subelem> [contents] = set Wi-Fi Display subelement
wfd_subelem_get <subelem> = get Wi-Fi Display subelement
fetch_anqp = fetch ANQP information for all APs
stop_fetch_anqp = stop fetch_anqp operation
interworking_select [auto] = perform Interworking network selection
interworking_connect <BSSID> = connect using Interworking credentials
interworking_add_network <BSSID> = connect using Interworking credentials
anqp_get <addr> <info id>[,<info id>]... = request ANQP information
gas_request <addr> <AdvProtoID> [QueryReq] = GAS request
gas_response_get <addr> <dialog token> [start,len] = Fetch last GAS response
hs20_anqp_get <addr> <subtype>[,<subtype>]... = request HS 2.0 ANQP information
nai_home_realm_list <addr> <home realm> = get HS20 nai home realm list
hs20_icon_request <addr> <icon name> = get Hotspot 2.0 OSU icon
fetch_osu = fetch OSU provider information from all APs
cancel_fetch_osu = cancel fetch_osu command
sta_autoconnect <0/1> = disable/enable automatic reconnection
tdls_discover <addr> = request TDLS discovery with <addr>
tdls_setup <addr> = request TDLS setup with <addr>
tdls_teardown <addr> = tear down TDLS with <addr>
tdls_link_status <addr> = TDLS link status with <addr>
wmm_ac_addts <uplink/downlink/bidi> <tsid=0..7> <up=0..7> [nominal_msdu_size=#] [mean_data_rate=#] [min_phy_rate=#] [sba=#] [fixed_nominal_msdu] = add WMM-AC traffic stream
wmm_ac_delts <tsid> = delete WMM-AC traffic stream
wmm_ac_status = show status for Wireless Multi-Media Admission-Control
tdls_chan_switch <addr> <oper class> <freq> [sec_channel_offset=] [center_freq1=] [center_freq2=] [bandwidth=] [ht|vht] = enable channel switching with TDLS peer
tdls_cancel_chan_switch <addr> = disable channel switching with TDLS peer <addr>
signal_poll = get signal parameters
signal_monitor = set signal monitor parameters
pktcnt_poll = get TX/RX packet counters
reauthenticate = trigger IEEE 802.1X/EAPOL reauthentication
autoscan [params] = Set or unset (if none) autoscan parameters
raw <params..> = Sent unprocessed command
flush = flush wpa_supplicant state
radio_work = radio_work <show/add/done>
vendor <vendor id> <command id> [<hex formatted command argument>] = Send vendor command
neighbor_rep_request [ssid=<SSID>] [lci] [civic] = Trigger request to AP for neighboring AP report (with optional given SSID in hex or enclosed in double quotes, default: current SSID; with optional LCI and location civic request)
erp_flush = flush ERP keys
mac_rand_scan <scan|sched|pno|all> enable=<0/1> [addr=mac-address mask=mac-address-mask] = scan MAC randomization
get_pref_freq_list <interface type> = retrieve preferred freq list for the specified interface type
p2p_lo_start <freq> <period> <interval> <count> = start P2P listen offload
p2p_lo_stop = stop P2P listen offload
dpp_qr_code report a scanned DPP URI from a QR Code
dpp_bootstrap_gen type=<qrcode> [chan=..] [mac=..] [info=..] [curve=..] [key=..] = generate DPP bootstrap information
dpp_bootstrap_remove *|<id> = remove DPP bootstrap information
dpp_bootstrap_get_uri <id> = get DPP bootstrap URI
dpp_bootstrap_info <id> = show DPP bootstrap information
dpp_auth_init peer=<id> [own=<id>] = initiate DPP bootstrapping
dpp_listen <freq in MHz> = start DPP listen
dpp_stop_listen = stop DPP listen
dpp_configurator_add [curve=..] [key=..] = add DPP configurator
dpp_configurator_remove *|<id> = remove DPP configurator
dpp_configurator_get_key <id> = Get DPP configurator's private key
dpp_configurator_sign conf=<role> configurator=<id> = generate self DPP configuration
dpp_pkex_add add PKEX code
dpp_pkex_remove *|<id> = remove DPP pkex information
Non-interactive mode,
- Set mixed mode security
$ wpa_cli -iwlan0 add_network
$ wpa_cli -iwlan0 set_network 0 auth_alg OPEN
$ wpa_cli -iwlan0 set_network 0 key_mgmt WPA-PSK
$ wpa_cli -iwlan0 set_network 0 psk '"12345678"'
$ wpa_cli -iwlan0 set_network 0 pairwise CCMP TKIP
$ wpa_cli -iwlan0 set_network 0 group CCMP TKIP
$ wpa_cli -iwlan0 set_network 0 mode 0
$ wpa_cli -iwlan0 set_network 0 ssid '"AndroidAP"'
$ wpa_cli -iwlan0 select_network 0
$ wpa_cli -iwlan0 enable_network 0
Connection to pure WPA3 networks
To support WPA3 via wpa_supplicant and networkmanager:- NetworkManager 1.16 released, adding WPA3-Personal and WireGuard support
- WPA3的支持是需要wpa_supplicant的版本>2.7 wpa_supplicant-2.9\wpa_supplicant\src.config:
CONFIG_SAE=yCheck STA's capabilities:
$ sudo wpa_cli get_capability key_mgmt Selected interface 'wlp0s20f3' NONE IEEE8021X WPA-EAP WPA-PSK OWE DPP FT-PSK SAEConfigure WPA3 in wpa_supplicant:
- Default configuration in the .conf file
key_mgmt=SAE psk="12345678" ieee80211w=1 # PMF
$ sudo ./wpa_supplicant -Dnl80211 -iwlan0 -c ../../wpa_0_8.conf -B
sudo ./wpa_cli -i wlan0 remove_network 0 sudo ./wpa_cli -i wlan0 ap_scan 1 sudo ./wpa_cli -i wlan0 add_network sudo ./wpa_cli -i wlan0 set_network 0 ssid '"WIFI_2g"' sudo ./wpa_cli -i wlan0 set_network 0 key-mgmt SAE sudo ./wpa_cli -i wlan0 set_network 0 psk '"12345678"' sudo ./wpa_cli -i wlan0 set_network 0 ieee80211w 1 sudo ./wpa_cli -i wlan0 select_network 0A quicker way to achieve the above is through direct manipulation of the connection file as follows:
sudo sed -i -e '/key-mgmt=/s,wpa-psk,sae,' /etc/NetworkManager/system-connections/mywifi.nmconnection
How to use WPA3 with Ubuntu 20.04
- wpasupplicant (2:2.9-1ubuntu4.3)
- network-manager (1.22.10-1ubuntu2.3)
- Identify your existing wifi connection
$ nmcli conn show NAME UUID TYPE DEVICE mywifi xxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx wifi wlp1s0
$ nmcli conn edit xxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx
nmcli> print wifi-sec.key-mgmt
802-11-wireless-security.key-mgmt: wpa-psk
nmcli> describe wifi-sec.key-mgmt
=== [key-mgmt] ===
[NM property description]
Key management used for the connection. One of "none" (WEP), "ieee8021x" (Dynamic WEP), "wpa-psk" (infrastructure WPA-PSK), "sae" (SAE) or "wpa-eap" (WPA-Enterprise). This property must be set for any Wi-Fi connection that uses security.
nmcli> set wifi-sec.key-mgmt sae
nmcli> verify
Verify connection: OK
nmcli> save persistent
Connection 'mywifi' (xxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx) successfully updated.
wpa_supplicant and Wi-Fi P2P
Wi-Fi CERTIFIED Wi-Fi Direct® enables Wi-Fi devices to connect directly to each other, Wi-Fi Direct devices connect to one another without joining a WiFi network.
Wi-Fi P2P is an optional component that needs to be enabled in the wpa_supplicant build configuration (.config). Here is an example configuration that includes Wi-Fi P2P support and Linux nl80211-based driver interface:
CONFIG_DRIVER_NL80211=y CONFIG_CTRL_IFACE=y CONFIG_P2P=y CONFIG_AP=y CONFIG_WPS=yActual Wi-Fi P2P operations are requested during runtime.
These can be done for example using wpa_cli .
wpa_cli starts in interactive mode if no command string is included on the command line.
By default, it will select the first network interface that it can find (and that wpa_supplicant controls).
If more than one interface is in use, it may be necessary to select one of the explicitly by adding -i argument on the command line (e.g., 'wpa_cli -i wlan1').
Establishing a peer-to-peer (P2P) link has the following phases:
- P2P discovery, which allows to search for P2P devices in the vicinity
- P2P group formation, a P2P group is formed with the identification of one of the devices as group owner. A device can either become group owner (GO) autonomously if configured to do so or it can be negotiated between devices with the exchange of GO intents.
- P2P provisioning, which authenticates the link by using either Push Button Configuration (PBC) or PIN authentication.
- P2P connection, when the connection between a Group Owner (GO) and a Group Client (GC) is actually established.
hostapd
hostapd is a user space daemon for access point and authentication servers. It implements:
- IEEE 802.11 access point management
- IEEE 802.1X/WPA/WPA2/EAP Authenticators
- RADIUS client
- EAP server
- RADIUS authentication server
The design goal for hostapd was to use hardware, driver, and OS independent, portable C code for all WPA functionality.
- The source code is divided into separate C files as shown on the code structure page.
- All hardware/driver specific functionality is in separate files that implement a well-defined driver API.
- Information about porting to different target boards and operating systems is available on the porting page.

- EAPOL (IEEE 802.1X) state machines are implemented as a separate module that interacts with EAP server implementation.
- Similarly, RADIUS authentication server is in its own separate module.
- Both IEEE 802.1X and RADIUS authentication server can use EAP server functionality.
- hostapd implements a control interface that can be used by external programs to control the operations of the hostapdt daemon and to get status information and event notifications.
- There is a small C library that provides helper functions to facilitate the use of the control interface.
Structure of the source code
wpa_supplicant implementation is divided into number of independent modules.
- wpa_supplicant core functionality
- wpa_supplicant.c Program initialization, main control loop
- main.c main() for UNIX-like operating systems and MinGW (Windows); this uses command line arguments to configure wpa_supplicant
- events.c Driver event processing; wpa_supplicant_event() and related functions
- wpa_supplicant_i.h Internal definitions for wpa_supplicant core; should not be included into independent
- Generic helper functions
- Cryptographic functions
- TLS library
- Configuration
- Control interface
- WPA supplicant
- EAP peer
- EAPOL supplicant
- Windows port
- Test programs
rfkill
simple tool for rfkill debugging/settings
crda
new central regulatory domain agent, nl80211 based userspace regulatory db agent
Regulatory
mac80211
mac80211 is a framework which driver developers can use to write drivers for SoftMAC wireless devices. SoftMAC is a term used to describe a type of Wireless module where the MLME( MAC Layer Management Entity ) is expected to be managed in software.



SoftMAC devices allow for a finer control of the hardware, allowing for 802.11 frame management to be done in software for them, for both parsing and generation of 802.11 wireless frames. Most 802.11 devices today tend to be of this type.
mac80211 implements the cfg80211 callbacks for SoftMAC devices, mac80211 then depends on cfg80211 for both registration to the networking subsystem and for configuration. Configuration is handled by cfg80211 both through nl80211 and
In mac80211 the MLME is done in the kernel for station mode (STA) and in userspace for AP mode (hostapd).
Open 802.11S Howto
802.11s
802.11s introduces routing capabilities at the MAC layer. Path selection is used to refer to MAC-address-based routing and to differentiate it from conventional IP routing.The DS(distribution system) allows APs to unite multiple BSSs to form an extended service set (ESS). Within an ESS, stations can roam from one BSS to another.
802.11s enables a new type of BSS, the so-called mesh BSS (MBSS).
Devices that form the mesh are called mesh stations (mesh STAs). Mesh stations forward frames wirelessly.
802.11s extends data and management frames by an additional mesh control field,

The mesh control field consists of:
- a mesh flags field The mesh flags field indicates the presence of additional MAC addresses in the mesh control field.
- a mesh time to live (TTL) field
- a mesh sequence number The TTL and sequence number fields are used to prevent the frames from looping forever.
- possibly a mesh address extension field The address extension allows for a total of 6 address fields in a mesh frame. This is useful when the source and destination of the frame are not part of the mesh, but are proxied by mesh stations. The proxied entities in the mesh address extension field can be identified as the final destination beyond the intermediate destination.
The mesh-specific beacon and probe frames contain a Mesh ID (the name of a mesh), a configuration element that advertises the mesh services, and parameters supported by the transmitting mesh station. This functionality enables mesh stations to search for suitable peers (e.g., other mesh stations that use the same path selection protocol and metric). Once such a candidate peer has been identified, a mesh station uses the Mesh Peer Link Management protocol to establish a peer link with another mesh station.
All beacon frames provide a time reference that is used for synchronization and power saving.
Power-saving mesh stations are either in light or deep-sleep mode:
- Being in light-sleep mode a mesh station switches to full power whenever a neighbor or the mesh station itself is expected to transmit a beacon frame.
- In deep-sleep mode a mesh station solely wakes up for its own beacon frame transmissions.
For medium access, mesh stations implement the mesh coordination function (MCF). MCF consists of a mandatory and an optional scheme:
- Enhanced Distributed Channel Access (EDCA)
- Mesh Coordinated Channel Access (MCCA) Mesh stations reserve TXOPs in the future called MCCA opportunities (MCCAOPs). An MCCAOP has a precise start time and duration measured in slots of 32 μs. To negotiate an MCCAOP, a mesh station sends an MCCA setup request message to the intended receiver. Once established, the mesh stations advertise the MCCAOP via the beacon frames. At the beginning of an MCCA reservation, mesh stations other than the MCCAOP owner prevent from channel access. The owner of the MCCAOP uses standard EDCA to access the medium. After an MCCA transmission ends, mesh stations use EDCA for medium contention again.
With 802.11s, mesh stations perform the dictionary attack-proof algorithm "Simultaneous Authentication of Equals (SAE)": A Secure, Password-Based Key Exchange for Mesh Networks.
SAE provides two mesh stations with a pairwise master key (PMK) that they use to encrypt their frame.
Within a mesh, all mesh stations use the same path metric and path selection protocol.
The default metric, termed airtime metric, indicates a link’s overall cost by taking into account data rate, overhead, and frame error rate of a test frame of size 1 kbyte.
The default path selection protocol, Hybrid Wireless Mesh Protocol (HWMP), combines the concurrent operation of a proactive tree-oriented approach with an on-demand distributed path selection protocol.
There is one root mesh station constantly propagates routing messages.
To provide compatibility with existing Wi-Fi devices, WFA’s marketing program requires each mesh station to incorporate either the AP or station functionality too. While Wi-Fi mesh APs must support frame-forwarding and thereby help to increase the radio coverage, non-AP mesh stations may choose to become an end station.
open80211s

open80211s, is an open-source implementation of the ratified IEEE 802.11s wireless mesh standard.
open80211s relies on Linux's mac80211 module, this module allows kernel to perform all necessary 802.11 frame management in software instead of in hardware. This arrangement is typicall called a SoftMAC approach, giving devices finer control of the hardware, allowing developers to upgrade the wireless stack without modifying the wireless card's firmware.
open80211s is part of the Linux kernel.
Driver requirements
Any mac80211 based driver should be open80211s capable, however non mesh-enabled mac80211 drivers may require minimal code changes in order to support open80211s.
Software Requirements
In order to set up a mesh you'll need a kernel and a few packages.
Using distro11s you can build a full mesh node using all the different repositories listed below and then runs all open80211s software in a virtualized QEMU instance.
Alternately, to build open80211s for a specific target you can fetch the different components individually and then compile each software module for your target platform:
- Open Mesh Just the Mesh ID and the channel must match. This is the simplest approach, it doesn't provide authentication or frame encryption, traffic is visible to any peer, similar to OPEN network for 802.11 AP/STA mode.
- kernel open80211s is part of the Linux kernel, any kernel published after September 2011 contains the open implementation of IEEE 802.11s standard. Configure the kernel to include the mac80211 stack with mesh capabilities using the config options:
- CONFIG_MAC80211
- CONFIG_MAC80211_MESH
- Secured Mesh All peers must share a secret password. Authentication is established via the Simultaneous Authentication of Equals protocol. Key derivation and cipher suite negotiation is done via the Authenticated Mesh Peering Exchange. Key derivation and cipher negotation is handle by userspace authsae application. authsae depends on openssl. You can get it via:
git://github.com/cozybit/authsae.gitthen build it.
Setup an Open Mesh network
Secured Mesh Setup using authsae
Wireless in Ubuntu
Configuring networking with nmcli
nmcli (NetworkManager Command Line Interface) is the command-line utility to configure networking through NetworkManager.
nmcli is used to create, display, edit, delete, activate, and deactivate network connections, as well as control and display network device status.
Each network device corresponds to a NetworkManager device. The configuration of a network device is completely stored in a single NetworkManager connection.
You can perform a network configuration by applying a NetworkManager connection to a NetworkManager device.
The basic format of using nmcli is:
nmcli [OPTIONS] OBJECT { COMMAND | help }
where
- OBJECT can be one of the following options:
- general
- networking
- radio
- connection
- device
- agent
- monitor
The most common nmcli commands:
- List the available network devices in the system
$ nmcli device
DEVICE TYPE STATE CONNECTION
eno1 ethernet connected Wired connection 1
wlp0s20f3 wifi connected Canonical-2.4GHz-g
virbr0 bridge connected virbr0
p2p-dev-wlp0s20f3 wifi-p2p disconnected --
p2p0 wifi unavailable --
lo loopback unmanaged --
virbr0-nic tun unmanaged --
A device can be:
- managed Under the NetworkManager control.
- unmanaged NetworkManager does not control it.
A managed device may be connected, meaning that it is activated and configured, or disconnected, meaning that it is not configured but ready to be activated again.
Most notable are: status, show, set, connect, disconnect, modify, delete, wifi.
Enter the nmcli device help command to see the full list.
Usage: nmcli device { COMMAND | help }
COMMAND := { status | show | set | connect | reapply | modify | disconnect | delete | monitor | wifi | lldp }
- status
- show [<ifname>]
- set [ifname] <ifname> [autoconnect yes|no] [managed yes|no]
- connect <ifname>
- reapply <ifname>
- modify <ifname> ([+|-]<setting>.<property> <value>)+
- disconnect <ifname> ...
- delete <ifname> ...
- monitor <ifname> ...
- wifi [list [ifname <ifname>] [bssid <BSSID>] [--rescan yes|no|auto]]
- wifi connect <(B)SSID> [password <password>] [wep-key-type key|phrase] [ifname <ifname>] [bssid <BSSID>] [name <name>] [private yes|no] [hidden yes|no]
- wifi hotspot [ifname <ifname>] [con-name <name>] [ssid <SSID>] [band a|bg] [channel <channel>] [password <password>]
- wifi rescan [ifname <ifname>] [[ssid <SSID to scan>] ...]
- wifi show-password [ifname <ifname>]
- lldp [list [ifname <ifname>]]
$ nmcli connection
NAME UUID TYPE DEVICE
Wired connection 1 26e29504-c881-3505-bd07-e77ed59f2acd ethernet eno1
Canonical-2.4GHz-g c3478c64-06b0-438a-a395-2bede1c9efb7 wifi wlp0s20f3
virbr0 496d1578-4d74-4cf0-8264-5997ebb27f02 bridge virbr0
se505 f0bfea7d-ffeb-49d0-bb36-c42298fcebdd wifi --
Every connection that is active is displayed as green on top of the list.The inactive connections are displayed as white.
The DEVICE field identifies the device on which the connection is applied on.
The nmcli connection command can take many arguments to manage connection profiles.
Most notable are: show, up, down, add, modify, delete.
Enter the nmcli connection help command to see the full list.
How to setup a Wifi hotspot with Network Manager
nmcli d wifi hotspot ifname wlan0 ssid test-hotspot password "test1234"shows the Wi-Fi name and password:
nmcli dev wifi show-passwordperform the following as root or sudo:
nmcli c add type wifi ifname WLAN_DEVICE_NAME con-name ARBITRARY_NAME autoconnect no ssid YOUR_SSID nmcli connection modify ARBITRARY_NAME 802-11-wireless.mode ap 802-11-wireless.band bg ipv4.method shared nmcli connection modify ARBITRARY_NAME wifi-sec.key-mgmt wpa-psk nmcli connection modify ARBITRARY_NAME wifi-sec.psk "YOUR_WIFI_PASSWORD" nmcli connection up ARBITRARY_NAMEIf your wifi device was wlp0s20f3, enter the following:
$ sudo apt install dnsmasq-base network-manager $ nmcli c add type wifi ifname wlp0s20f3 con-name ap-wlp0s20f3 autoconnect no ssid test-p2p Connection 'ap-wlp0s20f3' (e7fce4e0-7ba8-4f98-89aa-d2533c254dde) successfully added. $ nmcli connection modify ap-wlp0s20f3 802-11-wireless.mode ap 802-11-wireless.band bg ipv4.method shared $ nmcli connection modify ap-wlp0s20f3 wifi-sec.key-mgmt wpa-psk $ nmcli connection modify ap-wlp0s20f3 wifi-sec.psk "12345678" $ nmcli connection up ap-wlp0s20f3 Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/6)With these steps, everything is set for you:
- wifi gets configured for 10.42.0.0/24 network
3: wlp0s20f3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 34:2e:b7:a8:96:f2 brd ff:ff:ff:ff:ff:ff
inet 10.42.0.1/24 brd 10.42.0.255 scope global noprefixroute wlp0s20f3
valid_lft forever preferred_lft forever
inet6 fe80::4360:db0e:adfa:9715/64 scope link noprefixroute
valid_lft forever preferred_lft forever
$ ip route
default via 10.101.46.1 dev eno1 proto dhcp metric 100
10.42.0.0/24 dev wlp0s20f3 proto kernel scope link src 10.42.0.1 metric 600
10.101.46.0/24 dev eno1 proto kernel scope link src 10.101.46.138 metric 100
169.254.0.0/16 dev virbr0 scope link metric 1000 linkdown
192.168.122.0/24 dev virbr0 proto kernel scope link src 192.168.122.1 linkdown
There is one potential "gotchya".It is important you only install dnsmasq-base. Do NOT install the full dnsmasq package.
The full dnsmasq package will start dnsmasq as a service, and when you attempt to enable the access point with nmcli, the access point will not start because the dns port is already in use by the dnsmasq service.
Ubuntu 18.04. Driver for USB Wifi AC 12000 dual-band
This configuration item CONFIG_MT76x2U adds support for MT7612U-based wireless USB dongles.
$ lsmod | grep mt76x2u mt76x2u 24576 1 mt76x2_common 24576 1 mt76x2u mt76x02_usb 20480 1 mt76x2u mt76_usb 32768 2 mt76x02_usb,mt76x2u mt76x02_lib 69632 3 mt76x02_usb,mt76x2u,mt76x2_common mt76 53248 5 mt76_usb,mt76x02_lib,mt76x02_usb,mt76x2u,mt76x2_common mac80211 847872 5 mt76,mt76_usb,mt76x02_lib,mt76x02_usb,mt76x2u
- vendor: 0b05 ("ASUSTek Computer, Inc.")
- product: 17eb ("USB-AC55 802.11a/b/g/n/ac Wireless Adapter [MediaTek MT7612U]")
Error:
mt76x2u 1-4:1.0: vendor request req:07 off:09a8 failed:-110
About NetworkManager
NetworkManager is a system network service that manages your network devices and connections.
It manages Ethernet, WiFi, mobile broadband (WWAN) and PPPoE devices while also providing VPN integration with a variety of different VPN serivces.
By default network management on Ubuntu Core is handled by systemd's networkd and netplan.
The upstream NetworkManager project offers a wide range of features which are partially available in the snap version the following high level features:
- WiFi connectivity
- WWAN connectivity (together with ModemManager)
- Ethernet connectivity
Package: network-manager
network management framework (daemon and userspace tools).
- Manpage
$ dpkg -L network-manager | grep '/man/man.*/' | sort /usr/share/man/man1/nmcli.1.gz /usr/share/man/man1/nm-online.1.gz /usr/share/man/man1/nmtui.1.gz /usr/share/man/man1/nmtui-connect.1.gz /usr/share/man/man1/nmtui-edit.1.gz /usr/share/man/man1/nmtui-hostname.1.gz /usr/share/man/man5/NetworkManager.conf.5.gz /usr/share/man/man5/nm-settings.5.gz /usr/share/man/man5/nm-settings-keyfile.5.gz /usr/share/man/man5/nm-system-settings.conf.5.gz /usr/share/man/man7/nmcli-examples.7.gz /usr/share/man/man8/NetworkManager.8.gz
$ dpkg -L network-manager | grep service /lib/systemd/system/NetworkManager-dispatcher.service /lib/systemd/system/NetworkManager-wait-online.service /lib/systemd/system/NetworkManager.service /usr/share/dbus-1/system-services /usr/share/dbus-1/system-services/org.freedesktop.nm_dispatcher.service /lib/systemd/system/network-manager.service/usr/sbin/NetworkManager can be started by 2 services:
$ grep ExecStart /lib/systemd/system/NetworkManager.service /lib/systemd/system/network-manager.service /lib/systemd/system/NetworkManager.service:ExecStart=/usr/sbin/NetworkManager --no-daemon /lib/systemd/system/network-manager.service:ExecStart=/usr/sbin/NetworkManager --no-daemon
$ dpkg -L network-manager | grep init /etc/init.d /etc/init.d/network-manager
$ /etc/init.d/network-manager
Usage: /etc/init.d/network-manager {start|stop|restart|reload|force-reload|status}
$ service network-manager status
$ grep NetworkManager /var/log/syslog | grep WiFi Jun 8 14:07:18 jerry-System-Product-Name NetworkManager[966]: <info> [1591596438.5849] rfkill0: found WiFi radio killswitch (at /sys/devices/pci0000:00/0000:00:14.0/usb1/1-4/1-4:1.0/ieee80211/phy0/rfkill0) (driver mt76x2u) Jun 8 14:07:18 jerry-System-Product-Name NetworkManager[966]: <info> [1591596438.5850] manager[0x55c4cff57060]: rfkill: WiFi hardware radio set enabled Jun 8 14:07:18 jerry-System-Product-Name NetworkManager[966]: <info> [1591596438.7224] manager: rfkill: WiFi enabled by radio killswitch; enabled by state file Jun 8 14:07:19 jerry-System-Product-Name NetworkManager[966]: <info> [1591596439.2422] wifi-nl80211: (wlx2c4d54ccfca6): using nl80211 for WiFi device control Jun 8 14:07:19 jerry-System-Product-Name NetworkManager[966]: <info> [1591596439.2431] manager: (wlx2c4d54ccfca6): new 802.11 WiFi device (/org/freedesktop/NetworkManager/Devices/3)
$ grep NetworkManager /var/log/syslog | grep error Jun 7 20:46:23 jerry-System-Product-Name NetworkManager[1015]: <warn> [1591533983.4877] error requesting auth for org.freedesktop.NetworkManager.enable-disable-network: Authorization check failed: Action org.freedesktop.NetworkManager.enable-disable-network is not registered Jun 7 20:46:23 jerry-System-Product-Name NetworkManager[1015]: <warn> [1591533983.4883] error requesting auth for org.freedesktop.NetworkManager.sleep-wake: Authorization check failed: Action org.freedesktop.NetworkManager.sleep-wake is not registered Jun 7 20:46:23 jerry-System-Product-Name NetworkManager[1015]: <warn> [1591533983.4888] error requesting auth for org.freedesktop.NetworkManager.enable-disable-wifi: Authorization check failed: Action org.freedesktop.NetworkManager.enable-disable-wifi is not registeredNetworkManager uses DBUS communication between applications. The error indicates that data transmission and reception with the communication destination could not be performed in the DBUS communication. It occurred at the time of system startup and shutdown, it seems that polkitd start and end occurred around the start timing of NetworkManager. In that case, you can safely ignore the errors. If it occurs during operation, restart the polkit service with the following command:
# systemctl restart polkit
Debugging WiFi Connections
wpa_supplicant
Supplicant logging is normally directed to /var/log/wpa_supplicant.log.For wpa_supplicant 0.7 and later, this location is controlled by the /usr/share/dbus-1/system-services/fi.w1.wpa_supplicant1.service file.
$ cat /usr/share/dbus-1/system-services/fi.w1.wpa_supplicant1.ser [D-BUS Service] Name=fi.w1.wpa_supplicant1 Exec=/sbin/wpa_supplicant -u -s -O /run/wpa_supplicant User=root SystemdService=wpa_supplicant.serviceTo correctly and/or completely disable the wpa_supplicant service from running again in the future even after the network manager restarts and/or the system reboots is to mask the service, i.e.
$ sudo systemctl mask wpa_supplicant.service $ systemctl status wpa_supplicant.service
Debugging wpa_supplicant 0.7 and later
If your /usr/share/dbus-1/system-services/fi.w1.wpa_supplicant1.service file contains "-f /var/log/wpa_supplicant.log" on the Exec= line, then you can execute the following commands in a terminal to get verbose debug loggingUse NetworkManager to setup WiFi
Prepare
- Bring up WiFi Interface
$ sudo modprobe bcmdhd $ sudo ip link set wlan0 up
$ sudo snap install network-manager
$ nmcli dev show wlan0 ... GENERAL.STATE: 100 (connected) ...Check the GENERAL.STATE line:
- If WiFi is enabled, the state is either connected or disconnected.
- If WiFi is disabled the state is unavailable.
$ nmcli radio wifi on
Setup WiFi STA
- Change netplan configuration:
network:
ethernets:
all-en:
dhcp4: true
match:
name: en*
all-eth:
dhcp4: true
match:
name: eth*
version: 2
wifis:
wlan0:
access-points:
"2.4GHz-g":
password: "12345678"
dhcp4: yes
$ sudo netplan apply
- Listing available Wi-Fi APs
$ nmcli device wifi list
IN-USE SSID MODE CHAN RATE SIGNAL BARS SECURITY
Jerry_DSL Infra 1 270 Mbit/s 77 ▂▄▆_ WPA1
$ nmcli device wifi connect "Jerry_DSL" password "12345678"
$ sudo wpa_cli > interface wlan0 > scan_results ... 3c:ce:73:48:0e:40 2437 -63 [WPA2-PSK-CCMP][ESS] 2.4GHz-g ... > add_network 0 > set_network 0 ssid "2.4GHz-g" > set_network 0 psk "12345678" > enable_network 0
Setup WiFi P2P
- Change netplan configuration:
network: renderer: NetworkManager
$ sudo netplan apply
$ nmcli connection add type wifi ifname wlan0 con-name ap-wlan0 autoconnect no ssid test-p2p $ nmcli connection modify ap-wlan0 802-11-wireless.mode ap 802-11-wireless.band bg ipv4.method shared $ nmcli connection modify ap-wlan0 wifi-sec.key-mgmt wpa-psk $ nmcli connection modify ap-wlan0 wifi-sec.psk "12345678" $ nmcli connection up ap-wlan0 $ nmcli device DEVICE TYPE STATE CONNECTION wlan0 wifi connected ap-wlan0 lo loopback unmanaged -- $ nmcli connection NAME UUID TYPE DEVICE ap-wlan0 b1dfd4ba-2d63-4e15-9e1f-675e6c6e808a wifi wlan0 ap-wlan0 c15f7886-a68b-4342-bc89-bf27bf303336 wifi --
- Select the WiFi network “test-p2p”
- Join the network with password “12345678”
- ping the remote
$ ping 10.42.0.1
Setup WiFi AP
The benefit of using NetworkManager in this scenario is the complete automation of WiFi, DHCP server and NAT configuration.
- Disabling standalone dnsmasq service By default dnsmasq runs as a standalone service and will conflict with dnsmasq instance launched by NetworkManager.
To disable dnsmasq service:
$ sudo systemctl disable dnsmasq
$ sudo systemctl stop dnsmasq
[main]
dns=dnsmasq
# nmcli con add type wifi ifname wlan0 mode ap con-name WIFI_AP ssid MY_AP # nmcli con modify WIFI_AP 802-11-wireless.band bg # nmcli con modify WIFI_AP 802-11-wireless.channel 1 # nmcli con modify WIFI_AP 802-11-wireless-security.key-mgmt wpa-psk # nmcli con modify WIFI_AP 802-11-wireless-security.proto rsn # nmcli con modify WIFI_AP 802-11-wireless-security.group ccmp # nmcli con modify WIFI_AP 802-11-wireless-security.pairwise ccmp # nmcli con modify WIFI_AP 802-11-wireless-security.psk "11223344" # nmcli con modify WIFI_AP ipv4.method shared # nmcli con up WIFI_APnmcli also accepts wifi-sec and wifi strings instead of 802-11-wireless-security.
# reboot
Debug
- Showing general information and properties for a Wi-Fi interface
$ nmcli -p -f general,wifi-properties device show wlan0
Creating an access point with wpa_supplicant via dbus interface
Below is pretty self explanatory python code that's is trying to launch AP with the first interface (adapter) it have found.
import dbus
import sys
ssid = "TEST_WPA_DBUS_HOTSPOT"
frequency = 2412
bus = dbus.SystemBus()
wpa_sup_obj = bus.get_object('fi.w1.wpa_supplicant1', '/fi/w1/wpa_supplicant1')
props_iface = dbus.Interface(wpa_sup_obj, "org.freedesktop.DBus.Properties")
interfaces = props_iface.Get('fi.w1.wpa_supplicant1', "Interfaces")
try:
interface = interfaces[0]
except IndexError:
sys.exit("No interfaces availible")
print "Creating ap with %s" % (interface)
interface_obj = bus.get_object('fi.w1.wpa_supplicant1', interface)
interface_interface_props = dbus.Interface(interface_obj, "org.freedesktop.DBus.Properties")
interface_interface = dbus.Interface(interface_obj, "fi.w1.wpa_supplicant1.Interface")
adapters_name = interface_interface_props.Get("fi.w1.wpa_supplicant1.Interface", "Ifname")
print "Interface's name is %s" % adapters_name
key_mgmt = "NONE"
args = dbus.Dictionary({
'ssid': ssid,
'key_mgmt': key_mgmt,
'mode': 2,
'frequency': frequency
}, signature='sv')
netw = interface_interface.AddNetwork(args)
interface_interface.SelectNetwork(netw)
print "AP %s with frequency %i created with adapter %s" % ( ssid, frequency, adapters_name)
Note, that, after all, I've found wpa_supplicant not quite reliable for my needs (in my particular case, I wasn't able to launch 5GHz AP) and have switched to launching hostapd with different configuration files.
Setup 5 GHz Wifi access point using Atheros QCA6174A
QCA6174A-5: supports low power PCIe 2.1 (w/L1 substate) for WLAN and USB 1.1 interface for Bluetooth.
Installing hostapd
/etc/default/hostapd:DAEMON_CONF="/etc/hostapd/hostapd.conf" DAEMON_OPTS=""/etc/hostapd/hostapd.conf :
macaddr_acl=0 auth_algs=1 ignore_broadcast_ssid=0 #Support older EAPOL authentication (version 1) eapol_version=1 # Uncomment these for base WPA & WPA2 support with a pre-shared key wpa=3 wpa_key_mgmt=WPA-PSK wpa_pairwise=TKIP rsn_pairwise=CCMP wpa_passphrase=mysecret # Customize these for your local configuration... interface=wlan0 hw_mode=a channel=52 ssid=mywifi country_code=GDList all wireless devices and their capabilities:
# iw list [ ... ] Band 2: [ ... ]
$ modinfo ath10k_pci

留言