Full Disk Encryption (FDE)
Using the Ubuntu's Installer during the installation process
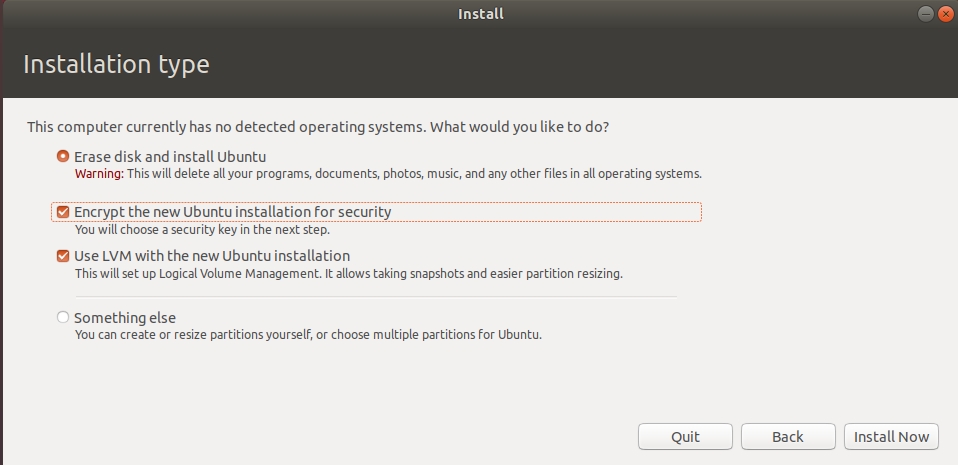
- Enable the Disk Encryption
- LVM is necessary and LVs will be created
- Input the key
- After installation, key is needed for every boot
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/mapper/ubuntu--vg-root 13166472 4403240 8074696 36% /
/dev/vda2 721392 169292 499636 26% /boot
/dev/vda1 523248 6268 516980 2% /boot/efi
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
vda 252:0 0 15G 0 disk
├─vda1 252:1 0 512M 0 part /boot/efi
├─vda2 252:2 0 732M 0 part /boot
└─vda3 252:3 0 13.8G 0 part
└─vda3_crypt 253:0 0 13.8G 0 crypt
├─ubuntu--vg-root 253:1 0 12.8G 0 lvm /
└─ubuntu--vg-swap_1 253:2 0 980M 0 lvm [SWAP]
$ sudo vgs
VG #PV #LV #SN Attr VSize VFree
ubuntu-vg 1 2 0 wz--n- 13.78g 0
Dm-crypt full disk encryption
The default cipher for LUKS is nowadays aes-xts-plain64, i.e. AES as cipher and XTS as mode of operation.XTS uses two possible key sizes are -s 256 and -s 512.
Generating an initramfs
After encrypting system or disk(s), one will need an initramfs so that rootfs can be mounted in there and then pass the control to real init.Initramfs is used to prepare Linux systems during boot before the init process starts.
The initrd will require parameters to tell it how to decrypt the drive, and they are supplied the same way as other kernel parameters. For example:
kernel /boot/kernel-3.4.0-gentoo crypt_root=UUID=encrypted partition uuid root=/dev/mapper/root
LUKS(Linux Unified Key Setup)
The Device-mapper is a component of the linux kernel (since version 2.6) that supports logical volume management.DM provides a generic way to create virtual layers of block devices that can do different things on top of real block devices.
The Device Mapper provides the foundation for a number of higher-level technologies such as LVM.
LVM logical volumes are activated using the Device Mapper.
Each logical volume is translated into a mapped device.
When LVM creates a volume, it creates an underlying device-mapper device that can be queried with the dmsetup command.
The Device Mapper supports a variety of mapping targets.
dm-crypt is such a device-mapper target that provides transparent encryption of block devices using the new Linux 2.6 cryptoapi.
The user can basically specify one of the symmetric ciphers, a key (of any allowed size), an iv generation mode and then the user can create a new block device in /dev.
Writes to this device will be encrypted and reads decrypted. You can mount your filesystem on it as usual. But without the key you can't access your data.
Cryptsetup is a utility used to conveniently set up disk encryption based on the DMCrypt kernel module.
Basic Guide To Encrypting Linux Partitions With LUKS
Setting up a basic encrypted partition on a Linux system is fairly easy. This is especially true when using LUKS, since its functionality is built directly into the kernel.- Installing Cryptsetup:
$ sudo apt install cryptsetup-bin
$ sudo cryptsetup luksFormat /dev/sdaxSome options can be used,
$ sudo cryptsetup -c aes-xts-plain64 --key-size 512 --hash sha512 --time 5000 --use-urandom /dev/sdaxCryptsetup will ask for a passphrase.
That will probably take a few seconds to complete, but when it's done, it will have successfully converted your partition into an encrypted LUKS volume.
$ sudo cryptsetup open /dev/sdax homeYou will be prompted for your passphrase.
$ sudo mkfs.ext4 /dev/mapper/homeThe one difference between creating the filesystem on a regular partition and an encrypted one is that you will use the path to the mapped name instead of the actual partition location. To fsck:
$ sudo fsck /dev/mapper/encrypted_volManually mounting and unmounting encrypted partitions is almost the same as doing so with normal partitions with one more step:
- mount
# cryptsetup --type luks open /dev/sdax encrypted_vol
# mount -t ext4 /dev/mapper/encrypted_vol /place/to/mount
# umount /place/to/mount
# cryptsetup close encrypted_vol
To make the encrypted volume to be mounted during the boot process:
- Find the UUID of the encrpted block device
$ sudo cryptsetup luksUUID /dev/sdax
home UUID=611a03bx-de4y-4f3z-a54a-acc6e9f4413b none luks,discard
At this point the mapping name is used to address the open luks volume.
/dev/mapper/home /home ext4 defaults 0 2
$ sudo update-initramfs -k all -cIf you see the following error:
I: Set the RESUME variable to override this.Change the file /etc/initramfs-tools/conf.d/resume:
RESUME=UUID=611a03bx-de4y-4f3z-a54a-acc6e9f4413bThen do it again.
$ sudo update-initramfs -k all -c update-initramfs: Generating /boot/initrd.img-5.8.0-25-generic update-initramfs: Generating /boot/initrd.img-5.8.0-26-generic
Encrypting disks on Ubuntu 19.04
In Ubuntu, there are several ways to encrypt your data.Disk encryption using LUKS
The Linux Unified Key Setup (LUKS) is the standard for Linux hard disk encryption.LUKS standardizes a partition header, as well as the format of the bulk data. LUKS can manage multiple passwords, that can be revoked effectively and that are protected against dictionary attacks with PBKDF2.
Allocate 15 GB virtual disk while creating the VM.
- Booting Ubuntu live image with “Try Ubuntu" option It’s required to create then encrypt partitions before installing Ubuntu.
- Creating partitions Use the graphic GParted application which is already installed on Ubuntu live image.
- Create a partition table on the VD Select the type "GPT".
- Create 3 partitions Created 3 partition:
- boot 500 MB, ext4.
- root 10 GB ext4.
- home 500 MB ext4.
- Encrypting root and home partitions cryptsetup - setup cryptographic volumes for dm-crypt (including LUKS extension).
cryptsetup <options> <action> <action args>
<action>:- create <name> <device> creates a mapping with <name> backed by device <device>.
- remove <name> removes an existing mapping <name>
- status <name> reports the status for the mapping <name>
- resize <name> resizes an active mapping <name>
- luksFormat <device> [<key file>] initializes a LUKS partition and sets the initial key, either via prompting or via <key file>.
- luksOpen <device> <name> opens the LUKS partition <device> and sets up a mapping <name> after successful verification of the supplied key material (either via key file by --key-file, or via prompting).
<options> can be [--hash, --cipher, --verify-passphrase, --key-file, --key-size, --offset, --skip, --readonly]
<options> can be [--cipher, --verify-passphrase, --key-size, --key-slot, --key-file (takes precedence over optional second argument), --keyfile-size, --use-random | --use-urandom, --uuid].
$ sudo cryptsetup luksFormat --hash=sha512 --key-size=512 /dev/vda2
$ sudo cryptsetup luksFormat --hash=sha512 --key-size=512 /dev/vda3
cryptsetup asks for input password before the initialization.After initializing a LUKS partition, the partition can be opened providing the passphrase.
$ sudo cryptsetup open --type=luks /dev/vda2 root
$ sudo cryptsetup open --type=luks /dev/vda3 home
Now LUKS partitions are available under /dev/mapper/:
$ ls -al /dev/mapper
total 0
drwxr-xr-x 2 root root 100 Nov 7 07:15 .
drwxr-xr-x 20 root root 4200 Nov 7 07:15 ..
crw------- 1 root root 10, 236 Nov 7 06:30 control
lrwxrwxrwx 1 root root 7 Nov 7 07:15 home -> ../dm-1
lrwxrwxrwx 1 root root 7 Nov 7 07:15 root -> ../dm-0
It’s recommended to clear the content on the LUKS partition:
$ sudo dd if=/dev/zero of=/dev/mapper/root bs=16M status=progress
$ sudo dd if=/dev/zero of=/dev/mapper/home bs=16M status=progress
- root
- Mark the physical partitions as a physical volumes
$ sudo pvcreate /dev/mapper/root Physical volume "/dev/mapper/root" successfully created.
$ sudo vgcreate vgroot /dev/mapper/root Volume group "vgroot" successfully created
$ sudo lvcreate -n lvroot -l 100%FREE vgroot Logical volume "lvroot" created.
- Mark the physical partitions as a physical volumes
$ sudo pvcreate /dev/mapper/home Physical volume "/dev/mapper/home" successfully created.
$ sudo vgcreate vghome /dev/mapper/home Volume group "vghome" successfully created
$ sudo lvcreate -n lvhome -l 100%FREE vghome Logical volume "lvhome" created.Use the graphical "Disks" application to display the partitions and volumes:
- Select “Something else” to assign encrypted partitions for /boot, / and /home.
- Make sure that the correct disk is selected as the “Device for boot loader installation”. /dev/vda.
- Configuring the boot partition /dev/vda1.
- Configuring the Encrypted logical volume lvroot Mounting the rlogical volume “/dev/mapper/vgroot-lvroot” to / and specifying ext4 to format it.
- Configuring the Encrypted logical volume lvhome Mounting the rlogical volume “/dev/mapper/vgroot-lvroot” to / and specifying ext4 to format it.
Mounting the boot partition to /boot and specifying ext4 to format it.
- Get the UUIDs of the encrypted partitions
$ sudo blkid /dev/vda2
$ sudo blkid /dev/vda3
- Mount partitions
sudo mount /dev/mapper/vgroot-lvroot /mnt
sudo mount /dev/vda1 /mnt/boot
sudo mount /dev/mapper/vghome-lvhome /mnt/home
sudo mount --bind /dev /mnt/dev
sudo chroot /mnt
mount -t proc proc /proc
mount -t sysfs sys /sys
mount -t devpts devpts /dev/pts
Adding following lines:
# <target name> <source device> <key file> <options>
root UUID=UUID_ROOT none luks,discard
home UUID=UUID_HOME none luks,discard
# update-initramfs -k all -cAfter restarting, Ubuntu prompted to enter the passphrase to unlock the disks at startup.
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/mapper/vgroot-lvroot 10009416 4368500 5112740 47% /
/dev/vda1 487634 89522 368416 20% /boot
/dev/mapper/vghome-lvhome 483670 6608 447571 2% /home
$ sudo vgs
[sudo] password for jerry:
VG #PV #LV #SN Attr VSize VFree
vghome 1 1 0 wz--n- 496.00m 0
vgroot 1 1 0 wz--n- 9.76g 0
$ lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
loop0 7:0 0 89.1M 1 loop /snap/core/8268
loop1 7:1 0 54.7M 1 loop /snap/core18/1668
loop2 7:2 0 44.9M 1 loop /snap/gtk-common-themes/1440
sr0 11:0 1 1024M 0 rom
vda 252:0 0 15G 0 disk
├─vda1 252:1 0 500M 0 part /boot
├─vda2 252:2 0 9.8G 0 part
│ └─root 253:0 0 9.8G 0 crypt
│ └─vgroot-lvroot 253:1 0 9.8G 0 lvm /
└─vda3 252:3 0 500M 0 part
└─home 253:2 0 498M 0 crypt
└─vghome-lvhome 253:3 0 496M 0 lvm /home
Full Disk Encryption Howto 2019
This page is focused on modifying the Ubuntu Desktop installer process in the minimum possible way to allow it to install with an encrypted /boot/ and root file-system.This is called almost Full Disk Encryption since the entire disk is never encrypted. What is encrypted are :
- the operating system partition
- the boot-loader second-stage file-system This includes the Linux kernel and initial RAM disk.
Prerequisites
Desktop installer ISO image .Boot the Installer
- Boot Modes PCs have two boot modes:
- BIOS (Basic Input Output System)
- UEFI (Unified Extensible Firmware Interface)
- First Boot Screen Choose Try Ubuntu without installing from the GRUB boot-loader menu.
- Live Desktop Once the Live Desktop environment has started we need to use a Terminal shell: to find and launch Terminal from the Show Applications button at lower-left corner.
- Pre-Prepare Encrypted Partitions
- Switch to root user
Choose Try Ubuntu.
$ sudo -i
# lsblk
If the installed target is /dev/sda, we'll set an environment variable we can re-use in all future commands.
# export DEV="/dev/sda"
- A small bios_boot (2MB) partition for BIOS-mode GRUB's core image
- an 128MB EFI System Partition
- a 768MB /boot/
- a final partition for the remaining space for the operating system.
First check for any existing partitions on the device and if some are found consider if you wish to keep them or not.
# sgdisk --print $DEV
You can also use the graphical user interface partitioning tool GPartEd from the Show Applications menu.The suntax to use sgfdisk to :create a partiton:
sgdisk --new=<partition_number>:<start>:<end> device
where start and end can be relative values, 0 means to adopt the lowest or highest possible value respectively.
To create 4 new partitons:
# sgdisk --new==1:0:+768M $DEV
# sgdisk --new==2:0:+2M $DEV
# sgdisk --new==3:0:+128M $DEV
# sgdisk --new==5:0:0 $DEV
After partitions are created, chyange the parameters for each partition:
- --typecode=partnum:{hexcode|GUID} Change a single partition's type code.
# sgdisk --typecode=1:8301 --typecode=2:ef02 --typecode=3:ef00 ---typecode=5:8301 $DEV
# sgdisk --change-name=1:/boot --change-name=2:GRUB ---change-name=3:EFI-SP --change-name=5:rootfs $DEV
GRUB only supports version 1 so we have to be explicit in the commands we use or else GRUB will not be able to install to, or unlock, the encrypted device.
- Encrypt the /boot/ partition
# cryptsetup luksFormat --type=luks1 ${DEV}1
# cryptsetup luksFormat ${DEV}5
# cryptsetup open ${DEV}1 LUKS_BOOT
# cryptsetup open ${DEV}5 ${DM}5_crypt
# ls /dev/mapper/
After the Ubuntu installation is finished we will be adding key-files to both of these devices so that you'll only have to type the pass-phrase once for GRUB and thereafter the operating system will use embedded key-files to unlock without user intervention.
- for the boot partition
# mkfs.ext4 -L boot /dev/mapper/LUKS_BOOT
# mkfs.vfat -F 16 -n EFI-SP ${DEV}3
- Initializes a physical volume(PV)
# pvcreate /dev/mapper/${DM}5_crypt
# vgcreate ubuntu-vg /dev/mapper/${DM}5_crypt
# lvcreate -L 4G -n swap_1 ubuntu-vg
# lvcreate -l 80%FREE -n root ubuntu-vg
- -L specify the size of the LV
- -n name the LV
- Choose the installation language and keyboard and then the software installation choices: choose the minimal installation
- In the Installation Type options choose Something Else
- The manual partitioner will start
- Select the root file-system device for formatting (/dev/mapper/ubuntu--vg-root) Press the Change button, choose Use As Ext4... and Mount point /
- Select the swap device (/dev/mapper/ubuntu--vg-swap_1) Press the Change button, choose Use as swap area
- Select the Boot file-system device for formatting (/dev/mapper/LUKS_BOOT),
- The installation process will continue in the background...
- Enable Encrypted GRUB Switch to the Terminal to configure GRUB:
# echo "GRUB_ENABLE_CRYPTODISK=y" >> /target/etc/default/grub
This has to be done before the installer reaches the Install Bootloader stage at the end of the installation process.If installation is successful choose the Continue Testing option to back to the terminal.
# mount /dev/mapper/ubuntu--vg-root /target
# for n in proc sys dev etc/resolv.conf; do mount --rbind /$n /target/$n; done
# chroot /target
# mount -a
Within the chroot environment, install and configure the cryptsetup-initramfs package:- install
# apt install -y cryptsetup-initramfs
The key-file and supporting scripts are added to the /boot/initrd.img-$VERSION files.
# echo "KEYFILE_PATTERN=/etc/luks/*.keyfile" >> /etc/cryptsetup-initramfs/conf-hook
# echo "UMASK=0077" >> /etc/initramfs-tools/initramfs.conf
Then generate a key-file,
- Generate a random key file
# mkdir /etc/luks
# dd if=/dev/urandom of=/etc/luks/boot_os.keyfile bs=4096 count=1
# chmod u=rx,go-rwx /etc/luks
# chmod u=r,go-rwx /etc/luks/boot_os.keyfile
# cryptsetup luksAddKey ${DEV}1 /etc/luks/boot_os.keyfile
# cryptsetup luksAddKey ${DEV}5 /etc/luks/boot_os.keyfile
# echo "LUKS_BOOT UUID=$(blkid -s UUID -o value ${DEVP}1) /etc/luks/boot_os.keyfile luks,discard" >> /etc/crypttab
# echo "${DM}5_crypt UUID=$(blkid -s UUID -o value ${DEVP}5) /etc/luks/boot_os.keyfile luks,discard" >> /etc/crypttab
Finally, pdate the initial ramfs files to add the cryptsetup unlocking scripts and the key-file:
# update-initramfs -u -k all













留言