LVFS: Linux Vendor Firmware Service
fwupd
Introduction
To update a BIOS or device firmware in Linux traditionally meant rebooting into Microsoft Windows, or preparing a MS-DOS floppy disk (!) and hoping that everything would work after the update.
The LVFS only provides firmware once the original OEM vendor has joined the project and uploaded files themselves.
The OEM vendor is in full control over what models are supported and is the only entity that can add support for new hardware.
fwupd is a simple daemon to allow session software to update device firmware on your local machine.
You can either use a GUI software manager like GNOME Software to view and apply updates, the command-line tool or the system D-Bus interface directly.
fwupdmgr
fwupdmgr is a command line fwupd client intended to be used interactively.Usage:
- To display all devices detected by fwupd
$ fwupdmgr get-devicesNote: Listed devices may not be updatable through fwupd (e.g. Intel integrated graphics).
Alternative vendor solutions may be provided instead.
$ fwupdmgr refresh
$ fwupdmgr get-updates
$ fwupdmgr update
GNOME Software
GNOME Software is an application store designed to make installing, removing and updating gracefully.When required, metadata files are automatically downloaded from the LVFS and submitted into fwupd over D-Bus.
- If there are updates that need applying then they are downloaded
- the user is notified and the update details are shown
- The user has to explicitly agree to the firmware update action before the update is performed.
$ sudo apt install gnome-software
Using the D-Bus API
The fwupd daemon is launched when queried for the first time.This exports an interface that can be queried from any language with a D-Bus binding
Setup for UEFI upgrade
The following requirements should be met:- Make sure you are booted in UEFI mode, it will not work in legacy boot mode.
- Verify your EFI variables are accessible.
- Mount your EFI system partition (ESP) properly. esp is used to denote the mountpoint in this section.
$ sudo ls /boot/efi/ EFI
LVFS
Introduction
The LVFS is a secure web service that can be used by OEM’s to upload firmware archives and can also be used by users to securely download metadata about available updates and optionally, the updates themselves.
The Problem
- what exact hardware they have installed
- where to look for updates
- specific flashing tools
The LVFS supplies the data in a secure format, allowing the fwupd project to install the update safely.
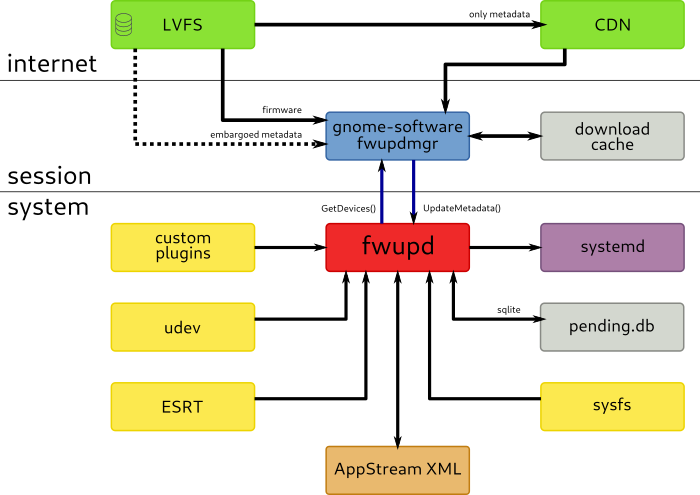
System Architecture
GNOME Software
For most desktop systems, at session start-up :- the metadata XML and detached signatures are checked for a specified age
- if required, newer files are automatically downloaded from the LVFS and pushed into fwupd over D-Bus.
- the fwupd daemon willl be queried over D-Bus for any pending updates.
- If there are updates that need applying then they are downloaded and the user is notified and the update details are shown in the specified language.
- The user has to explicitly agree to the firmware update action before the update is performed.
fwupd
This project provides a system-activated daemon fwupd with a D-Bus interface that can be used by unprivileged clients.Clients can perform system wide upgrades and downgrades according to a security policy, which uses PolicyKit to negotiate for authorization if required.
The command line tool fwupdmgr can be used to administer headless clients on the command line .
The daemon parses metadata in AppStream format from the LVFS along with a detached GPG or PKCS#7 signature.
LVFS
The LVFS provides an OEM-facing website that requires a username and password to access the secure console.This service should only be used to distribute firmware that is flashed onto non-volatile memory.
It is not designed for firmware that has to be uploaded to devices every time the device is used.
When .cab firmware files are submitted the following actions are performed:
- The update metadata in the archive is checked.
- The firmware capsule is signed with our GPG key or PKCS#7 certificate. Clients do not verify the signatures in the catalog file as this is for Windows Update only
- The new cab file is repacked. Only required files are included in the cabinet file, typically making the download size much smaller
- The metadata is added to our database.
Performance
- About 5% of the firmware downloads are performed using the fwupdmgr command line client manually
- 95% are done from the GNOME Software GUI program.
- There are currently over 160 devices supported on the LVFS with over 400 different firmware versions
Conclusions
The LVFS has grown to be an essential part of the Linux ecosystem and there are currently 26 vendors using the service.Various vendors are working on custom plugins for fwupd.
From a system administrators point of view, it will also soon be possible to get notified of updates and perform upgrades using the Cockpit framework as well as the usual client tools.
Getting an Account
Metadata
Uploading Firmware
Firmware Testing
Online Tests
Various tests are performed on the firmware by the LVFS if a firmware format is set in the metainfo.xml file .The update protocol can be changed on the LVFS website, and the correct tests will be run automatically.
UEFI Capsule
Capsule updates should be uploaded with a valid CAPSULE_HEADER that contains a GUID listed in the metainfo.xml file.
typedef struct {
EFI_GUID CapsuleGuid;
UINT32 HeaderSize;
UINT32 Flags;
UINT32 CapsuleImageSize;
} EFI_CAPSULE_HEADER;
DFU
DFU updates must be uploaded with a valid UFD footer that matches the device revision number with a correct CRC value.
dfu-tool allows a user to write various kinds of firmware onto devices supporting the USB Device Firmware Upgrade protocol.
This tool can be used to switch the device from the normal runtime mode to `DFU mode' which allows the user to read and write firmware.
Either the whole device can be written in one operation, or individual `targets' can be specified with the alternative name or number.
dfu-tool can convert a raw firmware image to include a DFU header, for example:
$ dfu-tool convert dfu old.raw new.dfu $ dfu-tool set-vendor new.dfu 0xabcd $ dfu-tool set-product new.dfu 0x1234
Blocklist
All binaries are scanned for specific strings which may indicate a problem with the firmware.Microcode
If a processor microcode is found then it is compared with older firmware versions that have been uploaded to the LVFS.PE Check
PE signatures will be checked.End-to-End testing
Claims
User Telemetry
Custom Protocol
Privacy Report
Offline Firmware
Deploy in immutable image
If the OS is shipped as an image, you can just install the .cab files into/usr/share/fwupd/remotes.d/vendor/firmwareand then enable vendor-directory.conf with
fwupdmgr enable-remote vendor-directory.
/usr/share/fwupd/remotes.d/vendor/firmware/README.md:
LVFS Releases
UEFI 膠囊更新 on Ubuntu Core
fwupgmgr 工具或命令可用來更新系統上的 UEFI BIOS。
沒有網際網路連線
- 到 secure-lvfs.rhcloud.com/lvfs/devicelist 下載最新的 .cab 檔案。
- 檢查目前的 BIOS 詳細資料。
$ sudo uefi-fw-tools.fwupdmgr get-devices
$ sudo cp firmware.cab /root/snap/uefi-fw-tools/common/
$ sudo uefi-fw-tools.fwupdmgr get-details [Full path of firmware.cab]
$ sudo uefi-fw-tools.fwupdmgr install [Full path of firmware.cab] -v
$ sudo reboot
具有網際網路連線
- 連接並登入 Edge Gateway。
- 檢查目前的 BIOS 詳細資料。
$sudo uefi-fw-tools.fwupdmgr get-devices
$sudo uefi-fw-tools.fwupdmgr refresh
$sudo uefi-fw-tools.fwupdmgr get-updates
$sudo uefi-fw-tools.fwupdmgr update -v
$ sudo reboot

留言