Wi-Fi Protected Setup
How does Wi-Fi Protected Setup work?
There are three primary approaches to network setup within Wi-Fi Protected Setup: push-button, PIN entry, and Near Field Communication (NFC). PIN entry is mandatory in all Wi-Fi Protected Setup devices, while push-button and NFC are optional and may also be found in some devices.
Push-button configuration (PBC): in some Wi-Fi Protected Setup networks, the user may connect multiple devices to the network and enable data encryption by pushing a button. The access point/wireless router will have a physical button, and other devices may have a physical or software-based button. Users should be aware that during the two-minute setup period which follows the push of the button, unintended devices could join the network if they are in range.
PIN entry: in all Wi-Fi Protected Setup networks, a unique PIN (Personal Identification Number) will be required for each device to join the network. A fixed PIN label or sticker may be placed on a device, or a dynamic PIN can be generated and shown on the device's display (e.g., a TV screen or monitor). PIN is used to make sure the intended device is added to the network being set up and will help to avoid accidental or malicious attempts to add unintended devices to the network.
A registrar device (which could be an Access Point/wireless router, PC television, or other device) will detect when a new Wi-Fi device is in range, and prompt the user to enter the PIN, if he or she wishes to add the new device to the network. In this mode, Wi-Fi Protected Setup network encrypts data and authenticates each device on the network. The PIN entry method is supported in all devices.
Near Field Communication (NFC): A Near Field Communication interface can be used to transfer network settings to a new device without requiring manual entry of its PIN. The NFC method provides strong protection against adding an unintended device to the network. This is an optional method for Wi-Fi Protected Setup Access Points and devices.
The vulnerability discovered in WPS makes that PIN highly susceptible to brute force attempts. Home routers will protect themselves after several failed attempts to authenticate as an external registrar by entering a lock-down state. During the lock-down state, all WPS attempts using the Router PIN will not work. The router will return from the lock-down state after a predetermined time period. While the router device is in a lock-down state, users can still use the WPS Push Button method to connect to the wireless network.
Since only the Router PIN method is vulnerable to brute force attack, disabling this function to best protect your network from invasion.
Wi-Fi Protected Setup Specification
Wi-Fi Simple Configuration Technical Specification Version 2.0.2
Introduction
Definitions
- Domain: A set of one or more Devices governed by a common authority for the purpose of gaining access to one or more WLANs.
- Enrollee: A Device seeking to join a WLAN Domain. Once an Enrollee obtains a valid credential, it becomes a Member.
- In-band: Data transfer using the WLAN communication channel
- Out-of-band: Data transfer using a communication channel other than the WLAN
- Registration Protocol. A Registration Protocol is a (logically) three party in-band protocol to assign a Credential to the Enrollee. The protocol operates between the Enrollee and the Registrar and may receive support through a proxy.
- Registrar: An entity with the authority to issue and revoke Domain Credentials. A Registrar may be integrated into an AP, or it may be separate from the AP. A Registrar may not have WLAN capability. A given Domain may have multiple Registrars.
- External Registrar: A Registrar for an AP’s Domain that runs on a device separate from the AP
- PushButton Configuration (PBC): A configuration method triggered by pressing a physical or
logical button on the Enrollee and on the Registrar.
Core Architecture
Enrollee -- A -- APEnrollee -- E -- Registrar
AP -- M -- Registrar
Components and Interfaces
Architecture Overview
Wi-Fi Simple Configuration defines new 802.11 information elements (IE) that are included in beacons, probe requests and probe responses. The purpose of these IEs is to advertise the presence of devices that are capable of performing Wi-Fi Simple Configuration operations.
Interface E
The purpose of Interface E is to enable the Registrar to discover and issue WLAN Credentials to the Enrollee.
Interface M
It enables an external Registrar to manage a Wi-Fi Simple Configuration AP. Wi-Fi Simple Configuration uses the same protocol for setting up the AP Management interface as for issuing Credentials to Enrollee devices.Interface A
The function of Interface A is to enable discovery of the Wi-Fi Simple Configuration WLAN and to enable communication between the Enrollee and IP-only Registrars.
Registration Protocol
The Registration Protocol operates in two phases. The first round trip of the Registration Protocol is used to exchange public keys and other descriptive information between the Registrar and the Enrollee using messages named M1 and M2D or M2. The Enrollee sends M1, and the Registrar sends M2D or M2. The primary role of the first round trip is to enable presence and feature discovery and to exchange public keys.
If both the Registrar and Enrollee decide to proceed with the second phase of the Registration Protocol, three additional round trips may be performed to complete authentication and Credential provisioning.
Security Overview
In-band Configuration
Device Password
All devices supporting Wi-Fi Simple Configuration must provide at least one numeric Device Password (PIN) for initial setup that is unique and randomly generated per device.
Headless Devices
Headless devices (i.e., those without a display) are required by Wi-Fi Simple Configuration to include an 8-digit device password called a PIN (A PIN on a headless device is typically printed on a sticker or otherwise physically inscribed on the device).
Because a fixed PIN value is able to be reused, it is susceptible to active attack.
In addition to the PIN method, headless devices may implement the push button configuration (PBC) method (Devices with richer UIs may also optionally implement the PBC method).
The PBC method should only be used if no PIN-capable Registrar is available and the WLAN user is willing to accept the security risks associated with PBC.
Devices with Displays
If an Enrollee device advertises support for the Display Configuration Method, it is required to generate a fresh 4 or 8-digit PIN each time it runs the Registration Protocol and show this PIN on a display.Guidelines and Requirements for PIN values
Out-of-band Configuration
Initial WLAN Setup
Standalone AP
A standalone AP should include a Wi-Fi Protected Setup Registrar, issuing keys to Enrollees via the Registration Protocol.Legacy AP
AP with an External Registrar
EAP-based Setup of External Registrar
Ethernet-based Setup of External Registrar
Adding Member Devices
Ideally, a Wi-Fi Protected Setup AP should support multiple keys such that each Enrollee in a typical home network can be given its own independent Credential. However, it is permitted for the AP to support only a single WPA-Personal key shared by all devices.
When an Enrollee is initialized, it looks for Beacons from APs and sends probe-requests with the WSC IE into either selected networks or into each network sequentially.
It may also send probe-requests to each 802.11 channel with the WSC IE included.
The Enrollee should continue looking for selected Registrar flags in Beacons, probe-responses and any M2 messages and should cease scanning when it finds a Registrar indicating that it is prepared to configure it.
In-band Setup Using a Standalone AP/Registrar
This scenario applies both for adding Enrollees with APs with built-in Registrar capabilities as well as wireless external Registrars.

Setup steps:
- The Enrollee sends its Discovery data in a probe request to a Wi-Fi Simple Configuration AP. The AP or wireless Registrar responds with its own Discovery data in the probe response.
- The user is prompted to enter the Enrollee’s device password into the AP/Registrar using a keypad interface or an out-of-band channel.
- The Enrollee connects and initiates 802.1X using the identity “WFA-SimpleConfig-Enrollee-1-0”.
- The Enrollee and Registrar exchange messages M1-M8 to provision the Enrollee.
- The Enrollee disassociates and reconnects, using its new WLAN authentication Credential.
Out-of-band Setup Using a Standalone AP/Registrar
Out-of-band Setup Using an External Registrar
Secure Setup with Legacy AP
Mental model mapping
No-Security Out-of-band Setup Using a Standalone AP
Mental model mapping
Secondary Usage Models
Registration Protocol Definition
Message Encoding
Wi-Fi Simple Configuration TLV Data Format
Wi-Fi Simple Configuration encodes information as attributes in a binary type identifier, length and value (TLV) format:
| Byte Offset | Field Length | Field Name | Description |
|---|---|---|---|
| 0 | 2 bytes | AttributeType | Type identifier for the attribute |
| 2 | 2 bytes | DataLength | Length in bytes of the attribute’s data field |
| 4 | 0-0xFFFF Bytes | Data | Attribute data |
Wi-Fi Protected Setup attributes are simple data structures, but some are nested data structures that contain other TLV attributes.
The Wi-Fi Protected Setup Information Element complies with the IEEE 802.11 Information Element format:
In the Wi-Fi Simple Configuration Information Element, the Element ID has a value of 221 and OUI is hex 00 50 F2 04.
802.11 Management Frames
Initial discovery of Wi-Fi Simple Configuration devices is accomplished using 802.11 Information Elements in management frames (Beacon, Probe Request, and Probe Response).
Access Points must provide the Wi-Fi Simple Configuration IE in all Beacon and Probe Response frames to indicate support for WSC. Stations must provide the Wi-Fi Simple Configuration IE in all Probe Request frames to indicate support for WSC.
If the Enrollee decides to pursue a connection to the network, it initiates an 802.1X/EAP connection for the EAP-based Registration Protocol.
Beacon Frame
If the Wi-Fi Protected Setup Information Element is included in a beacon frame, it contains attributes presented and described in the table:   
| Attribute | R/O | Allowed Values |
|---|---|---|
| Version | R | 0x10 = version 1.0, 0x11 = version 1.1, etc. |
| Wi-Fi Protected Setup State | R | 1 = unconfigured, 2 = configured |
| AP Setup Locked | O | Must be included if value is TRUE |
| Selected Registrar | O | BOOL: indicates if the user has recently activated a Registrar to add an Enrollee. |
| Device Password ID | O | Device Password ID indicates the method or identifies the specific password that the selected Registrar intends to use. |
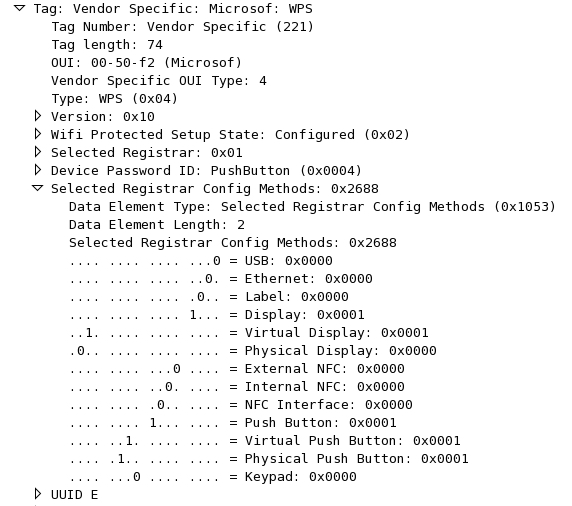
| Selected Registrar Config Methods | O | This attribute contains the config methods active on the selected Registrar. |
| UUID-E | O | The AP’s UUID is provided only when the AP is a dual-band AP in push button mode and indicating push button mode on both radios |
| RF Bands | O | Indicates all RF bands available on the AP. A dual-band AP must provide this attribute. |
| other... | O | Multiple attributes are permitted |
Association Request and Reassociation Request
If the Wi-Fi Protected Setup Information Element is included in an association request or reassociation request, it contains the following attributes:
| Attribute | R/O | Allowed Values |
|---|---|---|
| Version | R | 0x10 = version 1.0, 0x11 = version 1.1, etc. |
| Request Type | R | |
| other... | O | Multiple attributes are permitted |
Association Response and Reassociation Response
If the Wi-Fi Protected Setup Information Element is included in an association response or reassociation response, it contains the following attributes:| Attribute | R/O | Allowed Values |
|---|---|---|
| Version | R | 0x10 = version 1.0, 0x11 = version 1.1, etc. |
| Response Type | R | |
| other... | O | Multiple attributes are permitted |
Probe Request (D-E or D-R)
If the Wi-Fi Protected Setup Information Element is included in a probe request, it contains the following Enrollee device attributes:
| Attribute | R/O | Allowed Values |
|---|---|---|
| Version | R | 0x10 = version 1.0, 0x11 = version 1.1, etc. |
| Request Type | R | |
| Config Methods | R | |
| UUID-(E or R) | R | |
| Primary Device Type | R | |
| RF Bands | R | Specific RF band used for this message |
| Association State | R | |
| Configuration Error | R | |
| Device Password ID | R | |
| R | ||
| other... | O | Multiple attributes are permitted |
Probe Response (D-AP/Registrar)
If the Wi-Fi Protected Setup Information Element is included in a probe response, it contains the following attributes corresponding to the AP or Registrar using 802.11 ad hoc mode. If AP has locked its PIN, such as due to too many authentication failures, AP Setup Locked must be included. If Selected Registrar is TRUE, then the Selected Registrar, Device Password ID, and Selected Registrar Config Methods attributes MUST be included. Otherwise, they are omitted.
| Attribute | R/O | Allowed Values |
|---|---|---|
| Version | R | 0x10 = version 1.0, 0x11 = version 1.1, etc. |
| Wi-Fi Protected Setup State | R | 1 = unconfigured, 2 = configured. |
| AP Setup Locked | O | Must be included if value is TRUE |
| Selected Registrar | O | BOOL: indicates if the user has recently activated a Registrar to add an Enrollee. |
| Device Password ID | O | Device Password ID indicates the method or identifies the specific password that the selected Registrar intends to use.. |
| other... | O | Multiple attributes are permitted |
Push Button Configuration
Introduction
This section specifies an optional method called Push Button Configuration (PBC) that allows a Registrar with a very simple user interface (for example, a button and a LED) and no additional out-of-band channel to provide Credentials to PBC-capable Enrollee devices.PBC can be implemented in a variety of ways. On a limited-UI Registrar such as an AP, it could be implemented using only a button and a LED.
To simplify the discussion, this section uses the term button to describe the trigger element that initiates the PBC method on the Enrollee and Registrar.
Since the PBC method is unauthenticated, it is not permitted to use this method to manage AP settings.
User Experience
The PBC method requires the user to press a button on both the Enrollee and on the Registrar within a two-minute interval called the Walk Time.
PBC Technical Description
The button press or equivalent trigger event on the Enrollee (BE) causes it to actively search for a Registrar in PBC mode:
The Enrollee MUST complete a scan of all 802.11 channels that it supports to discover if any other nearby Registrars are in active PBC mode.
The Enrollee performs this scan by sending out probe requests with a Device Password ID indicating that the Enrollee is in PBC mode and receiving probe responses indicating a Selected Registrar with a PBC Device Password ID. The probe request and the probe response must include the WSC IE.
During this scan, if the Enrollee discovers more than one Registrar in active PBC mode then the Enrollee MUST abort its connection attempt and signal a “session overlap” error to the user.
Note: In the case of a dual-band AP and a dual-band station, the station may discover more than one Registrar in active PBC mode. If the dual-band station does discover more than one Registrar in active PBC mode, one on each RF band, and the UUID in the Beacon and Probe-Response are the same for all RF bands, then the station shall not consider this to be a session overlap.
If only one Registrar in active PBC mode is found after a complete scan, the Enrollee can immediately begin running the Registration Protocol with the Registrar in active PBC mode. The station must receive the Wi-Fi Simple Configuration IE from the Registrar, with active PBC mode, in order to engage with the Registrar using the PBC method.
- The Registrar must examine whether probe requests have been received within a 120 second window prior to the PBC button press on the Registrar. This window is called the PBC Monitor Time. Within the PBC Monitor Time, if the Registrar receives PBC probe requests from more than one Enrollee, or if the Registrar receives an M1 message from an Enrollee with a UUID-E that does not match the UUID-E received in a probe request, then the Registrar MUST signal a “session overlap” error. As a result, the Registrar must refuse to enter active PBC mode and must also refuse to perform a PBC-based Registration Protocol exchange until both of the following conditions are met:
The user presses the Registrar’s PBC button again.
Only one PBC Enrollee has been seen within the prior Monitor Time window of the new button press.
- If the Registrar is engaged in PBC Registration Protocol exchange with an Enrollee and receives a Probe Request or M1 Message from another Enrollee, then the Registrar should signal a “session overlap” error.
- If the Registrar has been running for less than Monitor Time (that is, it is freshly booted), it is not required to wait until Monitor Time has elapsed before entering active PBC mode.
- If the Registrar successfully runs the PBC method to completion with an Enrollee, that Enrollee’s probe requests are removed from the Monitor Time check the next time the Registrar’s PBC button is pressed. This permits multiple PBC Enrollees to be added sequentially without requiring a 120 second delay between each one.
PBC Security Considerations
If, for example, the end user presses the Registrar button first, the attacker has an opportunity to connect to the AP before the intended Enrollee’s button is pressed.
Data Element Definitions
The following table enumerates the various attribute types defined for Wi-Fi Simple Configuration.
- The overall size occupied by each attribute will include an additional 4 bytes (2 bytes of ID, 2 bytes of Length).
- Boolean attributes (identified with ‘Bool’ as the Length in the following table) have the Length of one byte (1B) and have two valid values: 0 = FALSE, 1 = TRUE.
- The variable length string attributes, e.g., Device Name, are encoded without null-termination, i.e., no 0x00 octets added to the end of the value. If the string is empty, the attribute length is set to zero.
- Note: Unrecognized attributes in messages must be ignored; they must not cause the message to be rejected.
| Description | ID(type) | Length | Detail |
|---|---|---|---|
| 802.1X Enabled | This variable specifies if the network uses 802.1X for network authentication. | ||
| AP Channel | This variable specifies the 802.11 channel the AP is hosting. | ||
| AP Setup Locked | This variable indicates that the AP has entered a state in which it will refuse to allow an external Registrar to attempt to run the Registration Protocol using the AP’s PIN (with the AP acting as Enrollee). The AP MUST enter this state after 3 failed PIN authentication attempts within 60 seconds. An AP must stay in the lock-down state for 60 seconds. When the AP is in this state, it MUST continue to allow other Enrollees to connect and run the Registration Protocol with any external Registrars or the AP’s built-in Registrar (if any). It is only the use of the AP’s PIN for adding external Registrars that is disabled in this state. | ||
| AppSessionKey | The AppSessionKey attribute allows the exchange of application specific session keys and may be used as an alternative to calculating AMSKs. | ||
| Application Extension | The Application Extension attribute is used to pass parameters for enabling applications during the WSC exchange. It is similar to the Vendor Extension attribute except that instead of a 3-byte Vendor ID prefix to the Vendor Data field, a 16-byte UUID (as defined in RFC 4122) is used. | ||
| Association State | The Association State component shows the configuration and previous association state of the wireless station when sending a Discovery request. | ||
| Authentication Type | This variable contains the selected value from the Authentication Types table for the Enrollee (AP or station) to use. | ||
| Authentication Type Flags | This variable indicates the network authentication capabilities of the Enrollee (AP or station). It provides a bitwise OR of the fields in the Authentication Types table. | ||
| Authenticator | The Message Authenticator component is a keyed hash of data. The specific data included in the hash calculation depends upon the processing context. | ||
| AuthorizedMACs | This subelement contains a list of Enrollee MAC addresses (each being six bytes in length) that have been registered to start WSC. The AP includes this field in Beacon and Probe Response frames so Enrollees can tell if they have been registered to start WSC. | ||
| Configuration Methods | 0x1008 | 2B | The Configuration Methods Data component lists the configuration methods the Enrollee or Registrar supports. The list is a bitwise OR of values . For ex.,
|
| Configuration Error | The Configuration Error component shows the result of the device attempting to configure itself and to associate with the WLAN | ||
| Confirmation URL4 | The Registrar may provide a URL (IPv4 address based) for the Enrollee to use to post a confirmation once settings have been successfully applied and the Enrollee has joined the network. | ||
| Confirmation URL6 | The Registrar may provide a URL (IPv6 address based) for the Enrollee to use to post a confirmation once settings have been successfully applied and the Enrollee has completed joining the network. | ||
| Connection Type | This attribute contains a specific value from the Connection Type Flags table for the Enrollee (AP or station) to use. | ||
| Credential | This is a compound attribute containing a single WLAN Credential. | ||
| Device Name | This component is a user-friendly description of the device encoded in UTF-8. | ||
| Device Password ID | This attribute is used to identify a device password. If the Device Password ID is Default, the Enrollee should use its PIN password (from the label or display). | ||
| EAP Identity | This attribute contains an ASCII representation of the NAI to be used with a Credential. | ||
| EAP Type | This attribute contains the binary representation of an EAP type as found in an EAP packet. | ||
| E-Hash1 | This is the HMAC-SHA-256 hash of the first half of the device password and the Enrollee’s first secret nonce. | ||
| E-Hash2 | This is the HMAC-SHA-256 hash of the second half of the device password and the Enrollee’s second secret nonce. | ||
| E-SNonce1 | This is the first nonce used by the Enrollee with the first half of the device password | ||
| E-SNonce2 | This is the second nonce used by the Enrollee with the second half of the device password. | ||
| Encrypted Settings | |||
| Encrypted Settings | The Data field of the Encrypted Settings attribute includes an initialization vector (IV) followed by a set of encrypted Wi-Fi Simple Configuration TLV attributes. | ||
| Encryption Type | This attribute contains a specific value from the Encryption Type Flags table for the Enrollee (AP or station) to use. | ||
| Encryption Type Flags | This attribute contains a binary OR set of WLAN encryption types supported by the Enrollee :
| ||
| Enrollee Nonce | The Enrollee Nonce component is a randomly generated binary value that is created by the Enrollee for setup. | ||
| Feature ID | This attribute indicates a particular feature build for an OS running on the device. | ||
| Identity | This attribute holds a user identity value encoded as an ASCII string. | ||
| Identity Proof | This attribute holds a proof of the claimed identity. | ||
| Key Identifier | This attribute contains a 128-bit key identifier. | ||
| Key Lifetime | This attribute contains the number of seconds until the Credential expires. | ||
| Key Provided Automatically | This variable specifies whether the key is provided by the network. | ||
| Key Wrap Authenticator | |||
| MAC Address | |||
| Manufacturer | The Manufacturer component is an ASCII string that identifies the manufacturer of the device. | ||
| Message Counter | This variable contains a 64-bit counter that is included in certain messages to prevent replay attacks. | ||
| Message Type | This variable identifies the specific message being sent by the Enrollee or Registrar:
| ||
| Model Name | |||
| Model Number | |||
| Network Key | This variable specifies the wireless encryption key to be used by the Enrollee:
| ||
| Network Key Sharable | This variable is used within Credential attributes. It specifies whether the Network Key included in this Credential can be shared or not with other devices. A TRUE value indicates that the Network Key can be shared. | ||
| New Device Name | This variable is used to change the friendly description of the device. | ||
| New Password | This variable is used to set a new password on the Enrollee. | ||
| Out-of-Band Device Password | The Out-of-Band Device Password attribute contains a fixed data structure intended to be compact enough to fit into small-capacity out-of-band channels. | ||
| OS Version | The OS Version component indicates what operating system is running on the device. | ||
| Permitted Configuration Methods | This variable contains the same data structure as Configuration Methods, but it indicates which of the Configuration Methods supported by the device are enabled. | ||
| Portable Device | This variable indicates that the device is portable. | ||
| Power Level | This variable indicates the power level in mW that the radio on the device is set to transmit. | ||
| Primary Device Type | This attribute contains the primary type of the device. | ||
| PSK Current | This variable represents the number of allocated PSKs on the AP. | ||
| PSK Max | This variable represents the maximum number of PSKs supported by the AP. | ||
| Public Key | This variable represents the sender’s Diffie-Hellman public key. | ||
| Public Key Hash | This variable contains the first 160 bits of the SHA-256 hash of a public key. | ||
| Selected Registrar | This field indicates that a Registrar has been selected by a user. If a user selects an Internal Registrar in AP and activates the registration protocol to accept new Enrollee, the Internal Registrar shall set the Selected Registrar attributes in the beacon and probe response frame to TRUE. In the case of External Registrar, External Registrar shall send a SetSelectedRegistrar UPnP action to AP with Selected Registrar attribute TRUE when the user has expressed an interest in adding a device. After the AP receives said SetSelectedRegistrar UPnP action with Selected Registrar TRUE, the AP incorporates Selected Registrar attribute set to TRUE in its beacons and probe responses. The AP shall update its Selected Registrar attribute based on the stateof all active Registrars. | ||
| Selected Registrar Configuration Methods | This attribute has the same values that Configuration Methods have. It is used in Probe Response messages to convey the Configuration Methods of the selected Registrar. | ||
| UUID-E | 0x1047 | 16B | The universally unique identifier (UUID) element is a unique GUID generated by the Enrollee. |
| UUID-R | 0x1048 | 16B | The universally unique identifier (UUID) element is a unique GUID generated by the Registrar. |
| Version | 0x104A | 1B(int) | |
| Wi-Fi Simple Configuration State | 0x1044 | 1B | For a Station Enrollee the 'Wi-Fi Simple Configuration State' attribute in WSC IE contained in Message M1 shall always have the value 'Not Configured' (0x01). For an Access Point, the Wi-Fi Simple Configuration State attribute in WSC IEs contained in beacon, probe response and message M1 indicates if the device is configured. |
The following table defines the subelement values used in WFA Vendor Extension attribute.
WFA Vendor Extension attribute is a Vendor Extension attribute (ID 0x1049) that uses Vendor ID 0x00372A and contains one or more subelements. Each subelement starts with a header consisting of one-octet ID field (the sublement ID value from the following table) and one-octet length field (number of octets in the payload of this subelement).
| Description | ID | Length |
|---|---|---|
| Version2 | 0x00 | 1B |
| AuthorizedMACs | 0x01 | <=30B |
| Network Key Shareable | 0x02 | Bool |
| Request to Enroll | 0x03 | Bool |
| Setting Delay Time | 0x04 | 1B |
| Reserved for future use | 0x05 to 0xFF |
Attribute types and sizes defined for Wi-Fi Simple Configuration:
Test Plan
Push Button Configuration
AP
Configure APUT: 4.1.5 Check PBC Walk Time is correctly implemented
After reset
- The Device PasswordID attribute in the WSC IE of the Beacon frame must NOT be present
- The Selected Registra flag is either NOT present, or if present, is set to zero(false)
Push the WSC button
- The Selected Registra flag in the WSC IE of the Beacon frame must be present and have the value TRUE
- The Device Password ID attribute needs to be set to PushButton (0x004)
After 2 minutes,
- The Device PasswordID attribute in the WSC IE of the Beacon frame must NOT be present
- The Selected Registra flag is either NOT present, or if present, is set to zero(false)
Add Devices: Add a STA device using PBC method
Turn on STA
Push the WSC button on the APUT
- The Selected Registra flag in the WSC IE of the Beacon frame must be present and have the value TRUE
- The Device Password ID attribute needs to be set to PushButton (0x004)
- Selected Registra Configuration Methods attribute in the WSC IE of the Beacon and Probe Response frame include PBC.
- If the APUT is dual band capable, the WSC IE of the Beacon and Probe Response must also contain the RF Bands and UUID-E attributes.


留言